If you’re an ISO 27001-compliant organization, it’s nearly time to start transitioning your Information Security Management System (ISMS) to the newest version, released in October 2022. Organizations have until October 24, 2025, to complete their transition to the 2022 version of the standard to maintain compliance.
For many, including our very own compliance team, transitional efforts will become a priority early next year. As you do this, you may be looking for a way to improve your cybersecurity, detect non-conformities, and collect evidence for an upcoming audit.
Field Effect MDR makes all three possible—and easy—especially with its latest ISO 27001:2022 Control Mappings. Let’s show you how.
Important changes to ISO 27001:2022
While there were some revisions to the high-level structure of the standard—clauses 4-10—the big changes came in the Annex A controls. In total, 11 new controls were introduced, three were removed, 23 were renamed, and 57 merged down to 24.
These new controls keep the ISO 27001 standard relevant in an age of increasing IT complexity and evolving cyber threats. The 2013 version, for example, had only one reference to cloud computing while the 2022 version has well over one hundred.
How can Field Effect MDR help?
Field Effect MDR alerts on security risks, vulnerabilities, and malicious behaviors with our proprietary ARO reporting format. Short for Actions, Recommendations, and Observations, AROs are prioritized, jargon-free alerts that include actionable instructions, or details of any automated actions taken, that make it easy for any organization to understand their next steps.
With the click of a button, AROs can map to the ISO 27001:2022 standard. That means alerts contain detailed advice on leveraging information from Field Effect MDR to prepare for your next audit.
Here are some examples.
Malware detected? Annex A 5.25
Field Effect MDR deploys a combination of signature and heuristic-based analytics. This combined approach ensures that well-understood threats are identified quickly and efficiently, while novel or emerging threats are also detected. Field Effect MDR can also take action to prevent malware installations and isolate impacted endpoint devices from the network, ensuring all types of malware are contained.
Upon detecting or stopping a malware threat, Field Effect MDR will issue an ARO, like this:
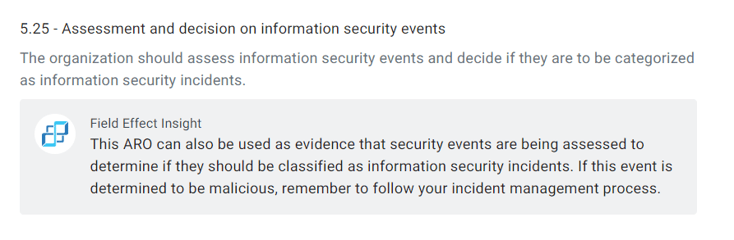
These reports can be used as proof during your next audit that security events are being assessed to determine if they’re malicious—a major requirement for control A 5.25 (Assessment and Decision on Information Security Events). It will also remind you to follow your incident management process if the event turns out to be an incident, like in cases of detected malware, like so:
Removable drive detected? Annex A 7.10
When Field Effect MDR detects USB activity, the ARO might remind the reader of control A 7.10 (Storage Media) and recommend that encryption be enabled on removable storage devices.
Here's an example of what you'd see:
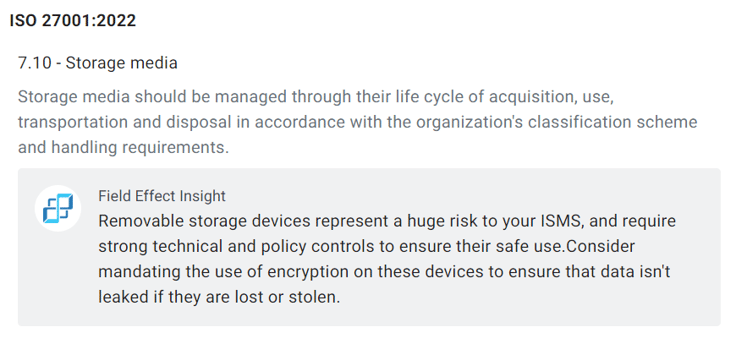
In addition, Field Effect MDR users will soon be able to further strengthen their implementation of this control by enabling USB blocking for unapproved devices.
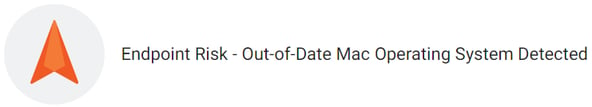
Outdated OS detected? Control A 8.8
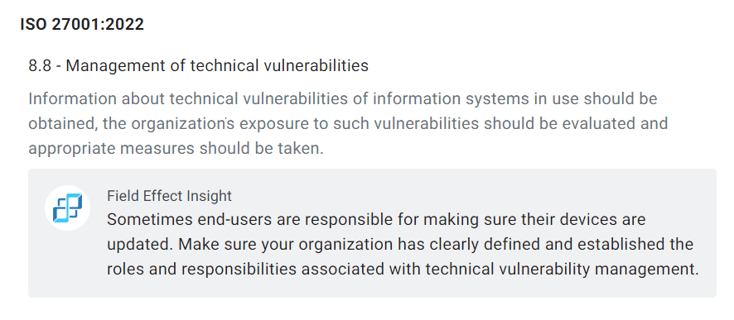
When Field Effect MDR detects an out-of-date operating system or other endpoint vulnerability it, will remind you of your obligations under control A 8.8 (Management of Technical Vulnerabilities) and provide clear visibility into which devices are affected, along with instructions on how to address the problem.
See below how Field Effect MDR recommends that you clearly document the roles and responsibilities within your vulnerability management program to comply with this control.
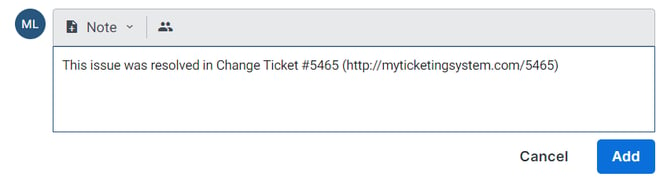
Plus, the Field Effect MDR’s internal note-making functionality makes it easy to show an auditor your vulnerability management program. By linking to the change ticket where the issue was resolved, you'll have all the evidence the auditor requires. From notification, to triage, to resolution—it’s all readily available.
Gain key threat intelligence for the new Annex A 5.7
One of the brand-new controls in ISO 27001:2022 is control A 5.7 (Threat Intelligence).
This control seeks to ensure that organizations understand the current cyber threat environment and use threat intelligence to mitigate new threats.
From a cybersecurity perspective, this makes perfect sense. But the reality is not all organizations have the resources to develop, implement, and maintain their own threat intelligence programs.
The good news is with Field Effect MDR you don’t have to. As a managed detection and response (MDR) solution, Field Effect MDR customers get world-class threat intelligence and active protection delivered by our dedicated team of experts.
Field Effect MDR's Monthly Service Report and our curated security intelligence feed help prove to auditors that you leverage threat intelligence to both prevent threats and reduce their impact.
Detect non-conformities before your auditor
Discovering a serious flaw in network architecture or security during an audit is a top fear among ISO implementors. Imagine an auditor identifying things like:
- Deprecated communication and encryption protocols
- Single-factor authentication
- Changes to networks performed without authorization
Field Effect MDR helps reduce this risk by continuously monitoring your network, cloud, and endpoints to detect and report on vulnerabilities and misconfigurations. If you want to learn more about how Field Effect MDR can not only strengthen your cybersecurity but also enhance your overall compliance posture, reach out to our team today.
