With the cost of data breaches reaching an all-time high in 2024, focusing on preventing attacks is more important than ever.
Instead of waiting for an attack to occur, proactively addressing risk to reduce the likelihood of attack not only minimizes the costs of a breach–including financial loss, operational downtime, reputational damage and recovery efforts—but improves your resilience to better prevent, withstand, and recover from cyberattacks. This inevitably leads to better cybersecurity and peace of mind.
Due to the intricacy of cyber risk management, many organizations will adopt a risk framework like NIST CSF, to apply industry best practices and comply with regulatory requirements. But structuring and executing a risk management strategy are two very different challenges.
Identifying and prioritizing all cyber risks facing an organization on an ongoing basis is both time-consuming and complex—requiring full visibility into your protected environment, a deep understanding of the threat landscape and the impact of cybersecurity risks, as well as the knowledge of how to address them.
Field Effect makes it easy to understand and manage risk as part of Field Effect MDR.
A simple approach to risk management
Field Effect empowers our partners and clients with the tools to prioritize and address the most critical cyber risks efficiently through a straightforward approach:
- Identify risks
- Prioritize the most critical risks for remediation
- Provide step-by-step instructions to remediate risk
- Monitor remediated risks and track them over time
Our approach aims to minimize the opportunities for attackers to target our customers, at the same time prioritizing early detection and containment in the event of a zero-day attack. By incorporating standard best practices into our solution, we assist our clients in achieving and maintaining compliance with leading regulatory frameworks.
Identify risks
Field Effect identifies cyber risk across IT environments, on the external attack surface, and in the dark web, with robust detections based on known and emerging risks.
With powerful visibility into the protected assets within an environment, Field Effect identifies and automatically responds to active threats on your behalf, while also pinpointing misconfigurations, vulnerabilities, and weaknesses that may make you an easy target for attackers.
Users can easily drill down into protected endpoints and cloud accounts to understand their environment and the risk associated with each asset. This includes unpatched software, end-of-life operating systems, and improperly configured antivirus settings, among others.
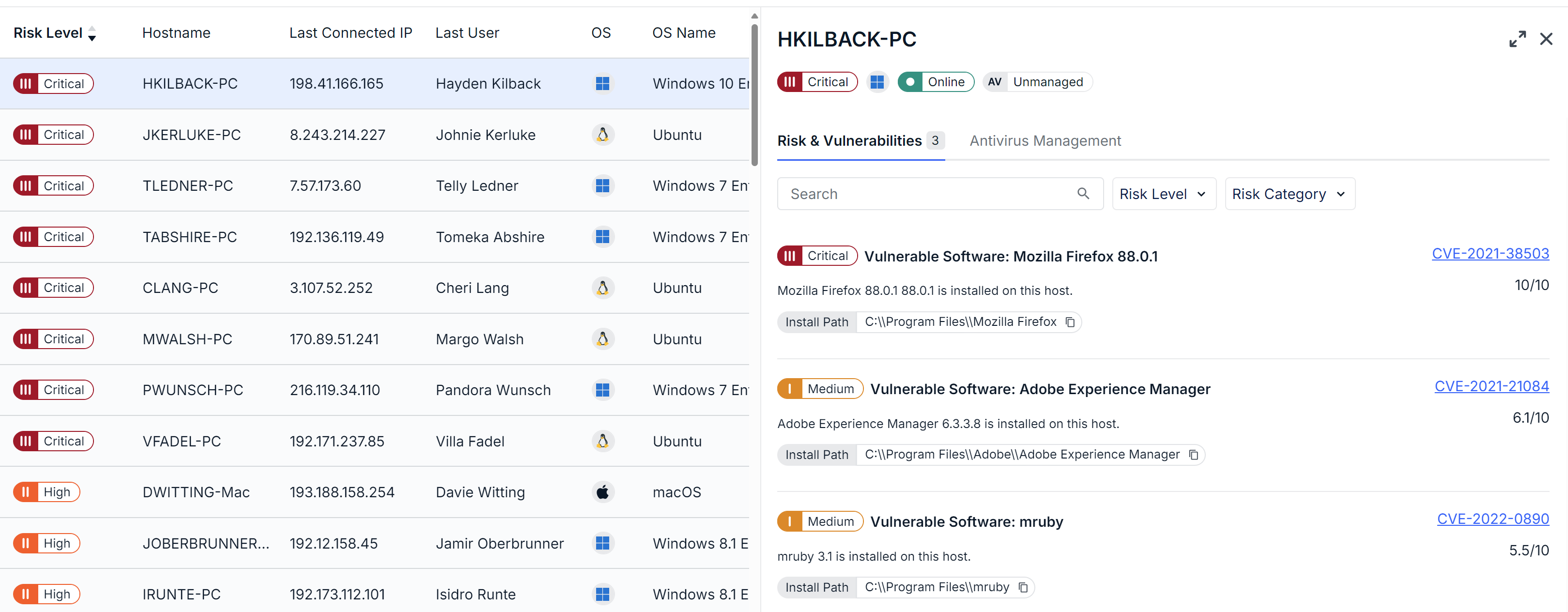
Field Effect’s Endpoint Devices Dashboard showcases all protected endpoints in one place, accompanied by a risk level of each device. Users can drill down into specific devices to see risks such as unpatched software, end-of-life operating systems, misconfigured AV settings, and more.
Prioritize the most critical risks for remediation
Field Effect's proprietary AROs (Actions, Recommendations, and Observations) automatically prioritize risks, helping clients focus their efforts effectively.
- Actions represent an active or imminent threat to an organization's cybersecurity posture. These AROs should be dealt with immediately as they alert of high-risk threats and/or vulnerabilities.
- Recommendations proactively report on risks detected within an organization. The risks categorized as a recommendation have the potential to evolve into bigger issues if left unattended.
- Observations are generated to flag early threat indicators and offer insight to strengthen security and reduce risk.
To provide an extra level of granularity, AROs are assigned a severity level, making it even easier to identify and address the most critical threats first.
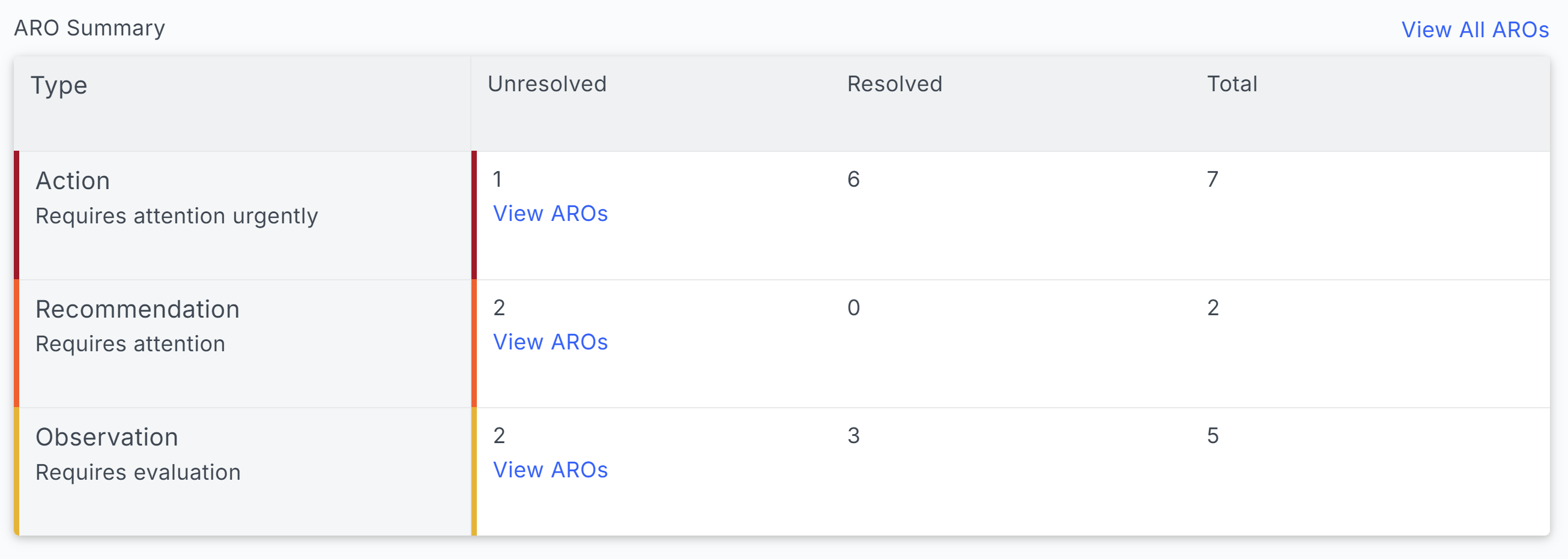
The ARO Summary view shows, at a glance, the total number of Actions, Recommendations, and Observations, and whether they've been tagged as resolved or still need to be addressed.
Provide step-by-step instructions to remediate risk
Each ARO is accompanied by a simple description of the identified risk, a summary of response actions taken, such as endpoint isolation or account isolation, and step-by-step remediation instructions so you can streamline recovery—no matter your technical background.
This approach helps eliminate any required time to triage the threat and determine the next steps, effectively minimizing the time and effort needed to remediate threats, which minimizes downtime and operational disruption.
For organizations aiming to achieve or maintain cybersecurity compliance, Field Effect maps AROs to regulatory requirements, highlighting compliance concerns. And if support is required—for compliance purposes or otherwise—you can contact Field Effect’s analysts with a single click of a button.
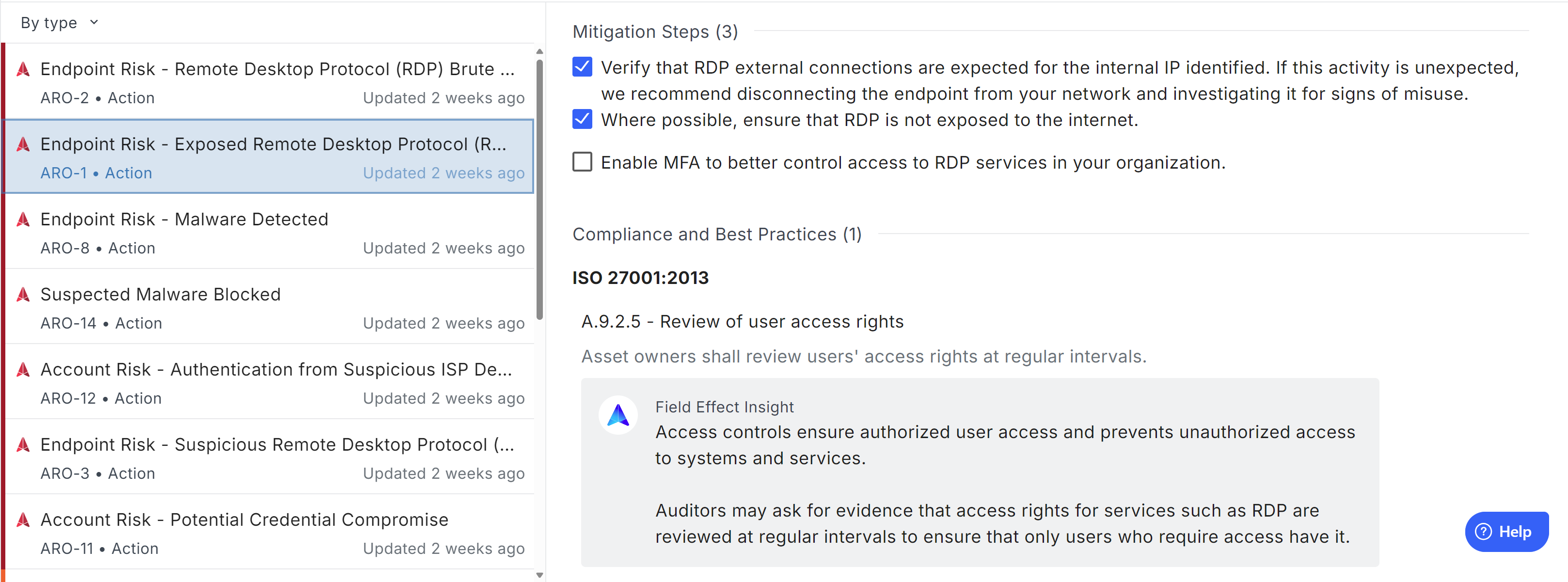
Clicking on an individual ARO will open a jargon-free summary of the issue identified, check-box style mitigation actions to take, as well as compliance information (if applicable and enabled).
Monitor remediated risks and track them over time
Once each ARO has been tagged as “Resolved” in the Field Effect MDR portal, we will ensure that the remediation steps have been successfully implemented and track risk over time.
You can reference Field Effect’s Risk Score to understand the impact of your patch management efforts on security posture and identify areas where additional effort is needed.
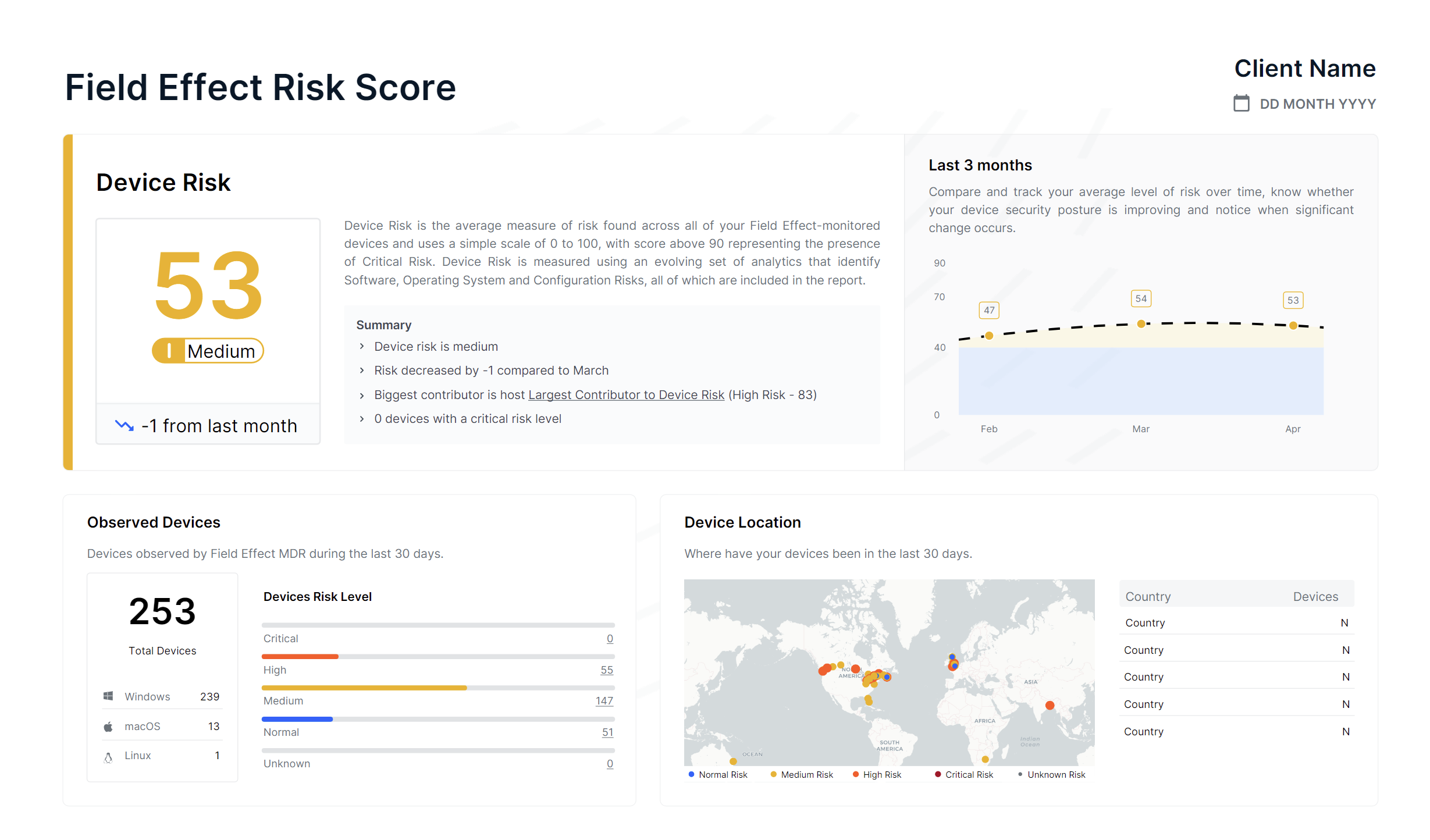
Like a report card, the Risk Score provides crystal-clear visibility into your overall risk level, a historical look at how you’ve improved over time, and where additional investment might be needed to strengthen your cybersecurity protection.
Delivering comprehensive protection
Up until recently, many cybersecurity solutions have focused on detecting and responding to "the boom,” otherwise known as a breach or attack. But why deal with an attack—and the inevitable fallout—if you could avoid it in the first place?
That’s why more and more businesses are choosing to stay ahead of threats by making left-of-boom tactics, including risk management, a key part of their cybersecurity strategy.
Whether you're focused on improving your cybersecurity or meeting regulatory requirements, Field Effect has got you covered. Field Effect MDR offers comprehensive protection to prevent, detect, and respond to threats in your environment, seamlessly integrating risk management into your overall cybersecurity strategy.
Want to see Field Effect MDR and its risk management capabilities in action? Watch the video here.
