On March 10, 2025, the social media platform X (formerly Twitter) experienced significant disruptions attributed to a massive cyberattack. Users worldwide reported intermittent outages throughout the day.
Elon Musk, owner of X, stated that the platform was under a "massive cyberattack," suggesting involvement from a large, coordinated group or possibly a nation-state. He noted that while X faces daily attacks, this incident was unprecedented in scale and resource intensity.
A pro-Palestinian hacker group known as Dark Storm Team claimed responsibility for the attack on its Telegram channel. Formed in 2023, Dark Storm has previously targeted government websites of NATO countries, Israel, and nations supporting Israel.
To mitigate the effects of the DDoS attack, X implemented Cloudflare’s DDoS-protection service, which shows a captcha when suspicious IP addresses connect to the site when a single IP address generates too many requests.
Investigations are ongoing to trace the exact origins and intentions behind the cyberattack.
Source: Bleeping Computer
Analysis
Dark Storm Team has, for nearly a year, been openly advertising its DDoS-for-hire services. Cybercriminal groups frequently engage in such activities, offering their botnets to third parties for financial or ideological motives.
Given this, it's plausible that Dark Storm did not target X out of its own initiative but instead acted on behalf of a paying client. The timing of the attack aligns with increased political pressure on Elon Musk, particularly regarding his involvement in U.S. government policy and his role in the Department of Government Efficiency.
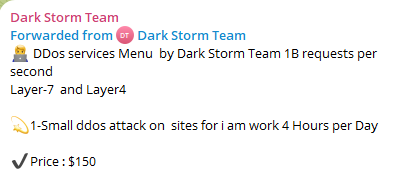
Image 1: Dark Storm Team advertising their DDoS platform can make one billion layer 4 and 7 requests per second (RPS). This is likely false as typical large-scale DDoS attacks range from 1 to 50 million RPS.
On the other hand, Dark Storm Team has historically launched attacks that align with its ideological leanings. Its previous operations have targeted NATO-aligned governments, Israeli institutions, and organizations seen as supporting Western interests.
If Dark Storm perceived Musk or X as aligned with these entities, then the attack could have been internally motivated. Furthermore, the group's public claim of responsibility suggests an attempt to bolster its reputation, which would be more in line with an independently driven attack rather than a covert, mercenary-style operation.
Ultimately, the true initiator of the attack remains unclear. While Dark Storm Team is more than capable of launching such a DDoS attack independently, the possibility that it was acting on behalf of a third party cannot be ignored.
Given Musk’s high-profile status and the contentious political landscape, there is a strong rationale for believing that the attack was financed or encouraged by an entity seeking to undermine him. Whether this was a nation-state, a corporate competitor, or a politically motivated group remains an open question that only a technical investigation into the attack’s origins can answer.
Mitigation
Field Effect’s Security Intelligence team constantly monitors the cyber threat landscape for threats like DDoS attacks. This research contributes to the timely deployment of signatures into Field Effect MDR to detect and mitigate the risk these threats pose.
Field Effect MDR users are automatically notified when various types of malicious activities are detected in their environment and are encouraged to review these AROs as quickly as possible via the Field Effect Portal.
Having a firewall will usually not stop the high volume of traffic generated during a DDoS attack, especially at the scale of those conducted against X. To properly mitigate this risk, organizations should deploy specific DDoS prevention solutions, like Cloudflare and Akamai, that are designed to counter various types and volumes of DDoS attacks.
Related Articles
