Field Effect Products
Outpace cyber threats with sophisticated cybersecurity solutions.
Detect and respond to threats across your whole business. Together, we can build your strongest defense.
Field Effect MDR
Cybersecurity for every business.
Sleep soundly knowing Field Effect MDR protects your entire business, all from one platform.
Backed by advanced analytics and human intelligence, Field Effect MDR detects and responds to threats across endpoints, networks, and cloud-based services.
Purpose-built to fit businesses of all sizes, Field Effect MDR deploys in minutes to start protecting you immediately. Plus, the platform’s revolutionary approach to alerting means you only receive the threat alerts that matter—putting time back in your day to focus on what's most important to you.
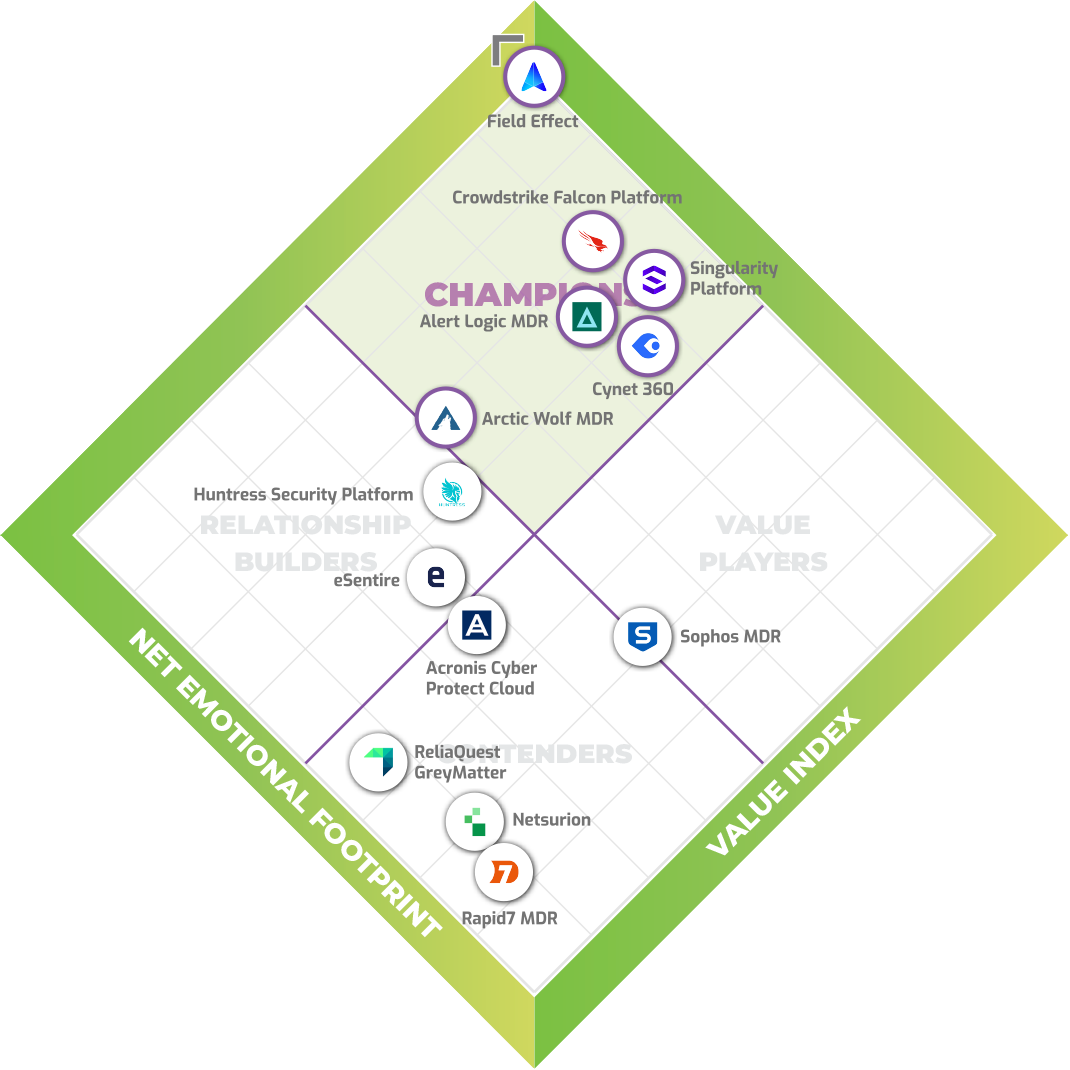
Trusted above the rest
Users rank Field Effect MDR the leading solution.
See what our users have to say



Get Started
Secure your business today.
Businesses of all sizes should have access to world-class cybersecurity. With Field Effect, they do.
Get a demo