Security researchers have discovered a critical zero-day vulnerability in Exim Mail Transfer Agent (MTA) software. The flaw, designated CVE-2023-42115, is caused by an out-of-bounds write error within MTA’s Simple Mail Transfer Protocol (SMTP) service.
The service doesn’t properly validate user-supplied data, which can result in data being written past the buffer. When successfully exploited, the flaw can lead to denial of service (via software crashes), data corruption, and the execution of remote commands.
CVE-2023-42115 was originally discovered and reported to Exim in June 2022, however, a patch is only expected to be released shortly. The security researchers attempted to contact Exim several times regarding CVE-2023-42115 and other vulnerabilities but ultimately weren’t satisfied with the lack of communication from Exim. Since the vulnerability had exceeded the disclosure timeline by several months, the researchers decided to disclose the bugs to the public.
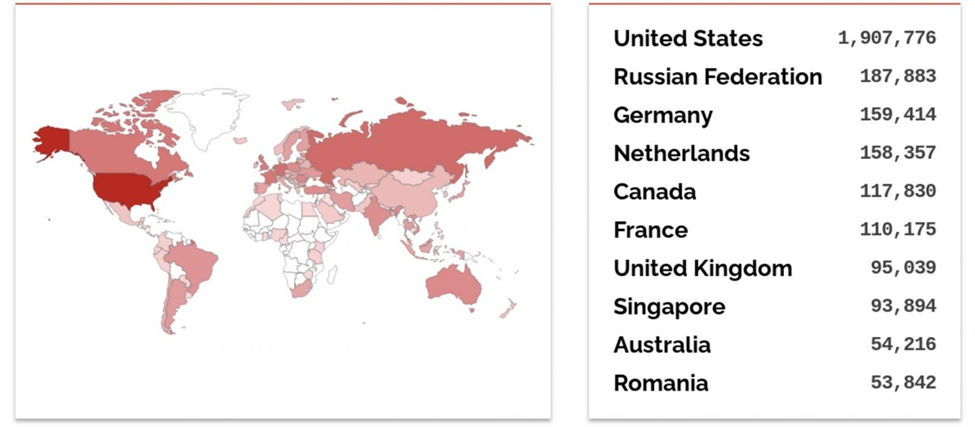
According to Shodan, approximately 3.5 million Exim servers are exposed to the internet, the vast majority located in the U.S.
Source: Bleeping Computer
Analysis
It’s unfortunate that Exim did not act sooner on the information that was responsibly disclosed to them by the researchers. However, it’s possible that Exim’s assessment of the vulnerability, including its criticality and conditions required for exploitation, differed from that of the researchers.
According to our analysis and research, an Exim MTA server must be configured in a certain way to be vulnerable to CVE-2023-42115. Specifically, its external authentication scheme must be configured and available. Furthermore, the limitations on the out-of-bounds written data make it very difficult for threat actors to design a functional exploit.
Since the patch is expected to be released within 24 hours, developing an exploit for this zero-day vulnerability is not worth the effort for most threat actors. However, given the valuable information that could potentially be obtained from a compromised mail server, it is likely that highly motivated and sophisticated threat actors will reverse engineer the upcoming patch to develop a functional exploit targeting unpatched Exim servers.
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities in software such as Exim MTA. Covalence users are automatically notified when vulnerable software, such as Exim MTA, is detected in their environment.
Field Effect recommends that organizations apply the appropriate patches once they are released by Exim.
Related articles
