Security Intelligence
Fortinet devices under increased targeting as AI-enabled attacks scale in 2026
Field Effect researchers observed increased targeting of Fortinet devices in early 2026, with attackers using...
Field Effect Managed Detection & Response (MDR) unifies endpoint, network, and cloud protection in one platform—with plain-language ARO alerts that cut noise and empower MSPs and IT teams.
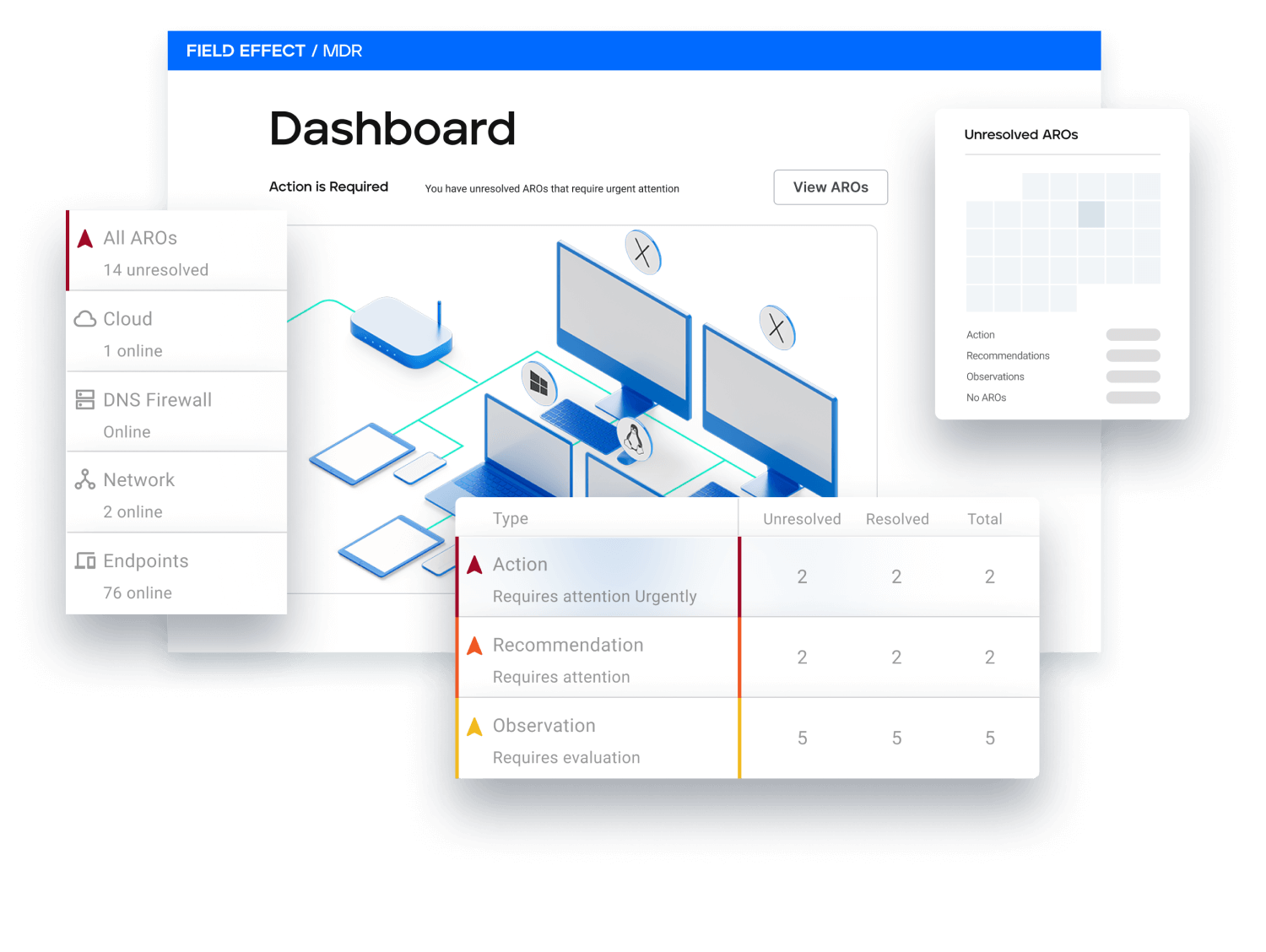
Field Effect MDR™ rapidly prevents, detects, and responds to threats all from one platform, minimizing complexity for you and maximizing defense for your clients.

.jpg)
Partner Program
Partner with us to deliver a differentiated cybersecurity service that attracts business, improves margins, and accelerates revenue growth.
Trusted above the rest





I have not only gained an amazing monitoring, detection, and response solution, but a team of cyber experts by my side.
Field Effect’s depth of cybersecurity knowledge and background in incident handling are impressive. We know we’re in great hands.
Professional Services
Whether you're experiencing an attack, need long-term cybersecurity guidance, or anything in between, we've got your back.
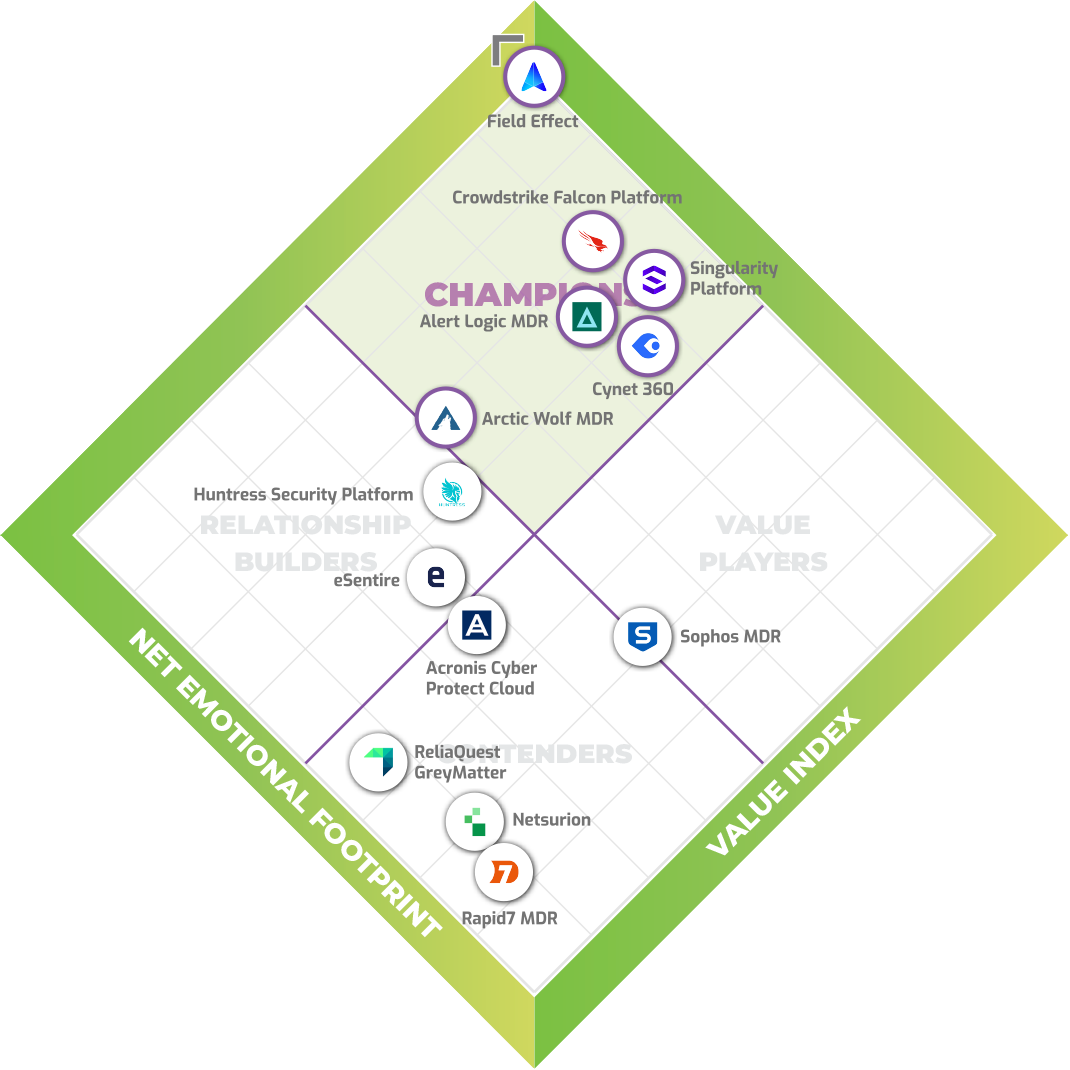
Awards & Recognition
Field Effect MDR is the top-rated managed detection and response solution in the Data Quadrant report for four years straight
2025
Field Effect MDR ranked #1 in the Emotional Footprint Awards, an annual report based solely on authentic user reviews
2025
Field Effect MDR wins in Cybersecurity Breakthrough Awards
2023
Field Effect MDR crowned Best Enterprise Machine Learning Solution
2022
Field Effect one of Canada's fastest-growing technology companies
2021

World-Class Cybersecurity Experts
Our mission is to revolutionize the cybersecurity industry by bringing advanced solutions and services to businesses of all sizes. With our sophisticated, yet easy to use and manage solutions, every business owner can get the hands-free cybersecurity they expect and the sleep-filled nights they deserve.
News & Intel

Security Intelligence
Field Effect researchers observed increased targeting of Fortinet devices in early 2026, with attackers using...

Security Intelligence
Iran-linked cyber activity involving Seedworm malware and compromised surveillance cameras highlights how IoT devices...

Security Intelligence
A pac4j-jwt flaw (CVE-2026-29000) allows attackers to bypass authentication by exploiting how encrypted JWTs are...
Get Started
Businesses of all sizes should have access to world-class cybersecurity. With Field Effect, they do.
Get a demo