Citrix is urging users of its NetScaler ADC and Gateway appliances to patch against two actively exploited zero-day vulnerabilities as soon as possible. The vulnerabilities, designated CVE-2023-6548 and CVE-2023-6549, affect the NetScaler management interface and could lead to remote code execution and/or denial of service (DoS) conditions on exposed and unpatched appliances.
Successful exploitation of CVE-2023-6548 requires the threat actor to log in to a low-privilege account with access to the management interface. To successfully conduct a DoS attack by exploiting CVE-2023-6549, the targeted appliance must be configured as a Gateway or authentication, authorization, and accounting (AAA) virtual server.
The flaws only impact customer-managed NetScaler appliances, leaving Citrix-managed cloud services and Adaptive Authentication unaffected.
According to data provided by Shadowserver, approximately 1,500 NetScaler management interfaces are exposed online, with the majority located in the US.
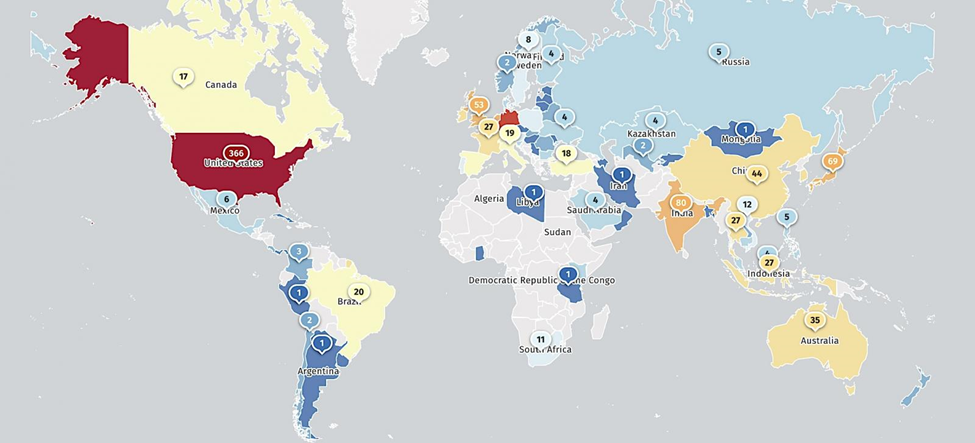
Scan results for exposed NetScaler Management Interfaces (Source: Shadowserver.org)
Source: Bleeping Computer
Analysis
Citrix’s NetScaler devices have a long track record of being exploited by nation-state actors and cybercriminals alike.
In November 2023, Citrix issued an urgent warning to its NetScaler ADC and Gateway users to kill all previous and active user sessions in addition to patching systems vulnerable to CVE-2023-4966, nicknamed “Citrix Bleed.” The extra mitigation step was required to prevent tokens stolen by threat actors during Citrix Bleed compromises from being used to enable persistent access even after the device is patched.
This warning coincided with the release of a joint advisory from the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI). The advisory contained indicators of compromise (IoCs), tactics, techniques, and procedures (TTPs), and detection methods associated with ransomware actor LockBit 3.0’s exploitation of the Citrix Bleed vulnerability to compromise a Boeing subsidiary. The exploitation led to 43GB of the company’s data being leaked on the dark web after it refused to pay the demanded ransom.
In 2019, APT 29, a group attributed to Russia’s Foreign Intelligence Service (SVR), exploited flaws in NetScaler ADC and Gateway devices to perform arbitrary code execution and deploy various malicious payloads, leading to the compromise of sensitive information and data.
Worse yet, in 2020, a ransomware attack exploiting Citrix vulnerability CVE-2019-19781 impacted the availability of systems at the University Hospital of Dusseldorf, resulting in the death of a patient.
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities discovered in devices like Citrix NetScaler ADC and Gateway. This research contributes to the timely deployment of signatures into Covalence, our flagship security solution, to detect and mitigate the exploitation of these vulnerabilities. Covalence users are automatically notified when devices are detected in their environment and are encouraged to review these AROs as quickly as possible.
Users of Citrix NetScaler ADC and Gateway devices should apply the latest security patch as soon as possible. Additionally, users should inspect access logs for suspicious activity.
Related articles
