Cisco has issued a warning today that a likely state-sponsored threat actor dubbed UAT4356 has been exploiting two zero-day vulnerabilities in its Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) firewalls to compromise government networks.
In a campaign dubbed ‘ArcaneDoor’, UAT4356 combined CVE-2024-20353 (a denial-of-service flaw) and CVE-2024-20359 (a persistent local code execution bug) to deploy two previously unknown implants and maintain persistence on ASA and FTD devices.
The first previously unknown implant, dubbed Line Dancer, is an in-memory shellcode loader that helps deliver and execute arbitrary shellcode payloads to disable logging, provide remote access, and exfiltrate captured packets.
The second implant, a persistent backdoor named Line Runner, comes with multiple defense evasion mechanisms to avoid detection and allows the attackers to run arbitrary Lua code on compromised firewalls.
Identify and reduce cyber risks with your free attack surface report.
Our quick, comprehensive attack surface reports detect end-of-life software, exposed devices and services, third-party risks & more.
Try it free
UAT4356 used the two implants collectively to modify configurations and conduct reconnaissance, network traffic capture/exfiltration and potentially move laterally.
Cisco has released security updates to address the two zero-day vulnerabilities and strongly recommends that users upgrade their devices as soon as possible to mitigate the threat of compromise. Cisco also encourages users to monitor system logs for any signs of unscheduled reboots, unauthorized configuration changes, or suspicious credential activity which may indicate compromise.
Source: Bleeping Computer
Analysis
As seen below, Cisco ASA and FTD firewalls are deployed worldwide and represent a relatively large attack surface for threat actors seeking access to the networks they protect.
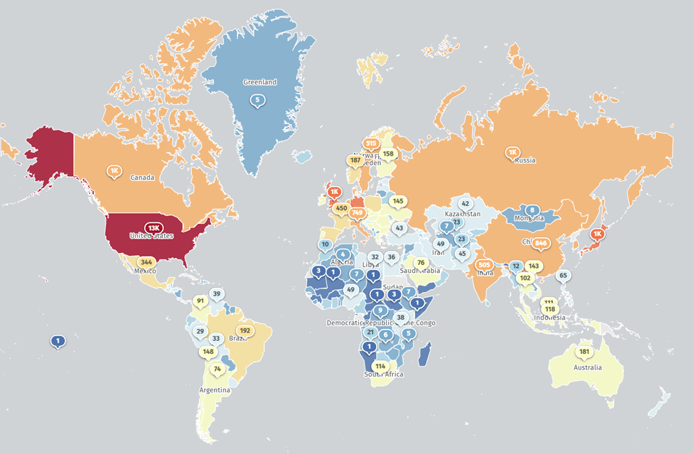
Image 1: Internet-exposed ASA firewalls (Source: Shadowserver Foundation)
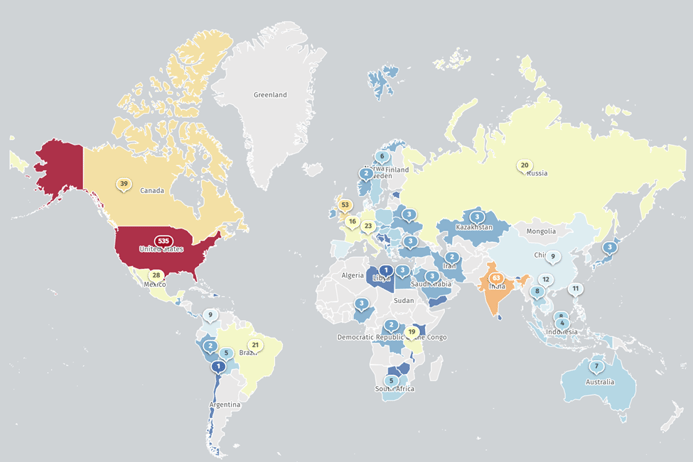
Image 2: Internet-exposed FTD firewalls (Source: Shadowserver Foundation)
Last week, Cisco released an update to address a high-severity flaw found in the command line interface (CLI) of its Integrated Management Controller (IMC) used by a lengthy list of its commercial-grade routers and switches. The flaw, designated CVE-2024-20295, is due to insufficient validation of user-supplied input and can be exploited with simple CLI commands made by a threat actor with read-only or higher privileges on the affected device. Successful exploitation could allow the threat actor to conduct command injection attacks and escalate their privileges to the root level.
Edge devices such as firewalls, switches, and routers are popular targets for threat actors seeking initial access to targets of interest. Control of these devices could allow threat actors to monitor/reroute traffic, obtain credentials that could be used to gain access to more sensitive systems and accounts, or as a platform to launch Adversary-in-the-Middle attacks.
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for threats emanating from campaigns like ‘ArcaneDoor’. This research contributes to the timely deployment of signatures into Field Effect’s MDR to detect and mitigate these threats.
Field Effect MDR users were automatically notified if an impacted Cisco device was detected in their environment, and are encouraged to review these AROs as quickly as possible via the Covalence portal.
Field Effect recommends that all other users of the affected Cisco devices install the security update according to Cisco’s advisory as soon as possible.
Related Articles
