The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is attributing a cyberattack on the Municipal Water Authority of Aliquippa in western Pennsylvania to the Iran-linked threat actor, Cyber Av3ngers.
According to CISA, Cyber Av3ngers targeted and compromised programmable logic controllers (PLCs) that are used by the water authority to control chemical levels, flow rates, and other processes associated with water and wastewater delivery and treatment.
The device, made by the Israeli company Unitronics, was likely accessed by exploiting inadequate cybersecurity practices, including weak passwords and unrestricted exposure to the internet. Other sources indicated that Cyber Av3ngers was able to take control of a booster station responsible for monitoring and regulating pressure for Raccoon and Potter townships in Pennsylvania.

Image 1: Screenshot of hacked Unitronics PLC
In response to the attack, the water authority advised there is no known risk to the municipality's drinking water or water supply since the affected system was immediately taken offline when the attack was detected.
Cyber Av3ngers has claimed it has infiltrated as many as 10 water treatment stations in Israel, plus a major cyber assault on Orpak Systems, a leading provider of gas station solutions. Explaining its focus on Israeli companies and manufactured equipment, Cyber Av3ngers advised on its Telegram channel that "Every Equipment 'Made in Israel' Is Cyber Av3ngers Legal Target.”
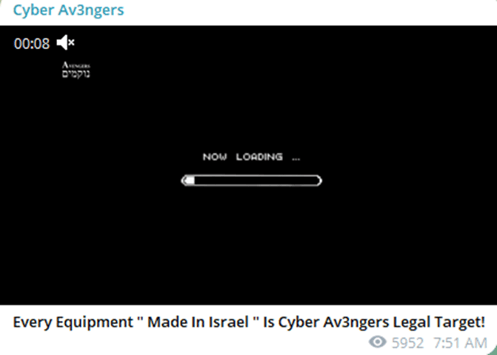
Image 2: Screenshot of Cyber Av3ngers warning (Source: Telegram)
To minimize the risk posed by such attacks, CISA recommends that organizations using Unitronics PLCs change the default password, enforce multi-factor authentication (MFA), disconnect the PLC from the internet, conduct backups of the logic and configurations to enable fast recovery, and apply the latest updates.
Source: The Hacker News
Analysis
This is the first known time that Cyber Av3ngers has targeted organizations operating outside of Israel. Cyber Av3ngers, however, did warn that it considers Israeli-manufactured equipment a legitimate target, regardless of its location.
According to a Shodan scan, there are over 1,800 Unitronics devices connected to the internet.
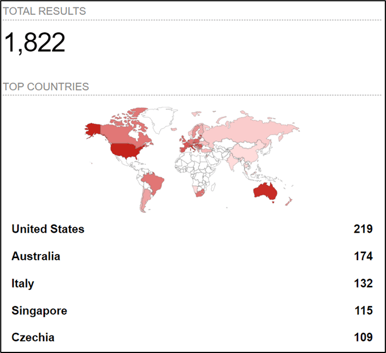
Image 3: Search results for Unitronics devices (Source: Shodan.io)
Interestingly, some of the hits returned by Shodan even display screenshots of the Unitronics PLC interface hosted on the IP:
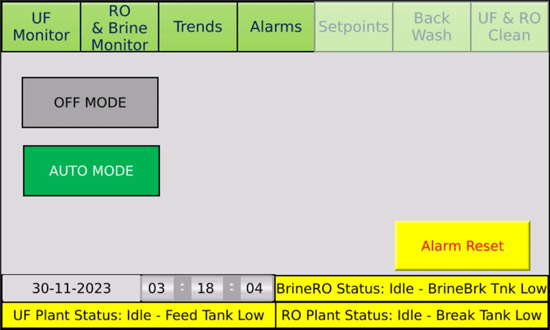
Image 4: Screenshot of Unitronics PLC interface (Source: Shodan.io)
Simply by filtering through the results, Field Effect was able to quickly identify a Unitronics PLC Model V570 named “Raccoon Primary PLC” residing on a Pennsylvania-based IP address, which could have been the PLC targeted and compromised by Cyber Av3gers.
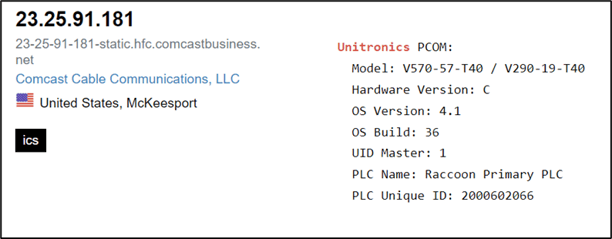
Image 5: Identification of Unitronics PLC named Raccoon Primary PLC (Source: Shodan.io)
Field Effect was unable to identify any known vulnerabilities in Unitronics PLCs, thus, Cyber Av3ngers was likely able to breach the affected PLC by using the default password, guessing the password, or performing a brute force attack on the device, rather than exploiting a zero-day vulnerability.
This isn’t the first time a threat actor has been able to breach a U.S.-based water utility.
In 2021, an employee working for a water treatment plant in Oldsmar, Florida reported that his computer mouse started moving on its own, navigated to the sodium hydroxide level control panel, and started to increase the level by more than 100 percent. The employee immediately pulled the plug on his computer and his vigilant supervisor noticed the attempted chemical level change and quickly reversed it.
The attack was never attributed to a specific threat actor but still served as a warning to utilities to improve the security of their industrial control systems.
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitors the cyber threat landscape for emerging threat actors like Cyber Av3ngers. This research contributes to the timely deployment of signatures into Covalence, our flagship security solution, to detect and mitigate the risk posed by threat actors. Covalence users are automatically notified when known TTPs of threat actors are detected in their environment and are encouraged to review these AROs as quickly as possible.
Field Effect encourages Unitronics users to familiarize themselves with the alert released by CISA and to adopt the following mitigative controls as soon as possible:
- Change the Unitronics PLC default password—validate that the default password “1111” is not in use.
- Require multifactor authentication (MFA) for all remote access to the OT network, including from the IT network and external networks.
- Disconnect the PLC from the open internet. If remote access is necessary, implement a Firewall/VPN in front of the PLC to control network access to the remote PLC. A VPN or gateway device can enable multifactor authentication for remote access even if the PLC does not support multifactor authentication. Unitronics also has a secure cellular-based long-haul transport device that is secure to their cloud services.
- Back up the logic and configurations on any Unitronics PLCs to enable fast recovery. Become familiar with the process of factory resetting and deploying configurations to a device in the event of being hit by ransomware.
- If possible, utilize a TCP port that is different than the default port TCP 20256. Cyber actors are actively targeting TCP 20256 after identifying it through network probing as a port associated to Unitronics PLC. Once identified, they leverage scripts specific to PCOM/TCP to query and validate the system, allowing for further probing and connection. If available, use PCOM/TCP filters to parse out the packets.
- Update PLC/HMI to the latest version provided by Unitronics.
Related articles
