Security researchers have developed a new method to exploit a critical vulnerability in Apache ActiveMQ. The remote code execution vulnerability, designated CVE-2023-46604, allows threat actors to run shell commands on vulnerable devices.
Apache released a patch for CVE-2023-46604 on October 25, however unpatched systems have become a popular target for ransomware and cybercrime groups using a crude proof-of-concept exploit code that was released in late October 2023. The new exploitation method allows threat actors to run shell commands in memory which doesn’t require saving tools to disk where they are more easily detected by antivirus programs.
Source: The Hacker News
Analysis
Given the public availability of a newer stealthier exploit code, it’s likely that more threat actors will soon take advantage of this vulnerability. A recent scan using Shodan.io revealed there are nearly 70,000 potentially vulnerable ActiveMQ instances deployed worldwide, leaving no shortage of targets for threat actors.
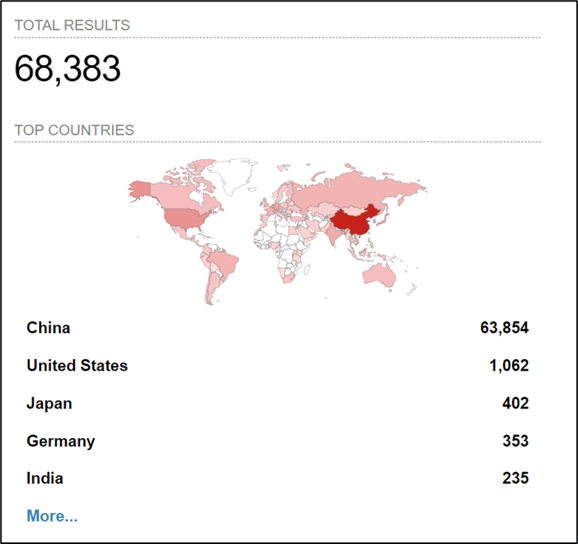
Image 1. Scan results for Apache ActiveMQ deployments. (Source: Shodan.io)
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities discovered in devices like Apache ActiveMQ. This research contributes to the timely deployment of signatures into Covalence, our flagship security solution, to detect and mitigate the exploitation of these vulnerabilities. Covalence users are automatically notified when devices are detected in their environment and are encouraged to review these AROs as quickly as possible.
Users of Apache ActiveMQ should apply the latest security patch as soon as possible, to mitigate the risk this vulnerability poses. Additionally, users should terminate all sessions post-upgrade in case they have been compromised and inspect access logs for suspicious activity.
Related articles
