Field Effect has detected a limited and brief phishing campaign that takes advantage of misconfigurations in open redirect scripts hosted on subdomains of large organizations and popular online marketplaces to send phishing links.
Analysis
The format of the phishing links caught our attention since at first glance they appear to originate from a reputable organization’s domain and may look legitimate to the recipient. However, upon analysis, we discovered that the URLs of the phishing links consisted of two distinct components.
First, the URL paths point to an ASPX (Active Server Page Extended) script called “go2.aspx”. The ASPX scripts are legitimately hosted on a subdomain of one of these reputable companies. Under normal circumstances, the ASPX script is intended to redirect webpage visitors between website resources within the company’s domain.
URL Path Example:
https://subdomain.companydomain.com/rts/go2[.]aspx
The second component of the URL is where the parameters are passed to the script, normally set as “h”, “tp”, and “X”. The two former parameters are used for tracking purposes; however, the “x” parameter represents the next URL to which the script should redirect the visitor.
URL Parameters:
h=1234567&tp=i-XXXX&x=www.companydomain[.]com
In the incidents we observed, the threat actors identified instances of the ASPX redirect script with insufficient validation and replaced the value of the “x” parameter causing the script to instead redirect to an external domain.
Legitimate Usage:
https://subdomain.companydomain.com/rts/go2.aspx?h=1234567&tp=i-XXXX&x=www.companydomain[.]com
Phishing Modification:
https://subdomain.companydomain.com/rts/go2.aspx?h=1234567&tp=i-XXXX&x=maliciousphishing[.]com
The modified URLs were sent as phishing links that ultimately led to a website designed to obtain Microsoft credentials and in some cases were hosted behind Cloudflare protection to prevent automated scanning.
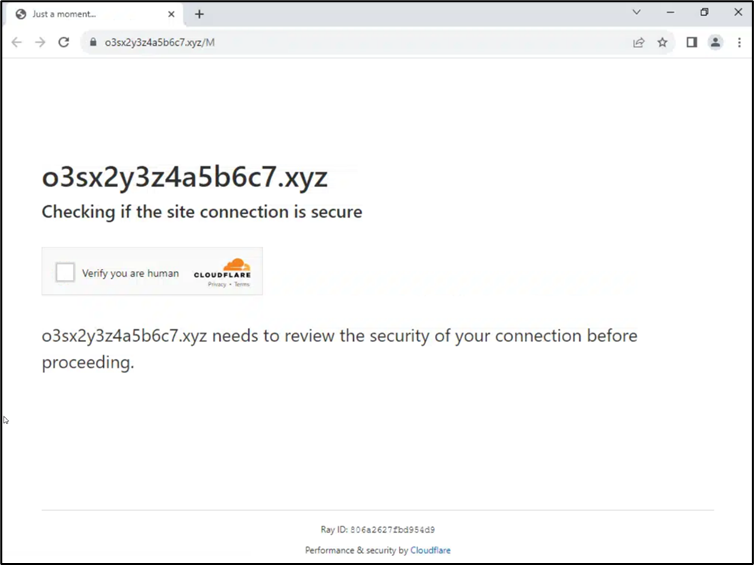
Image 1: Cloudflare protection redirect
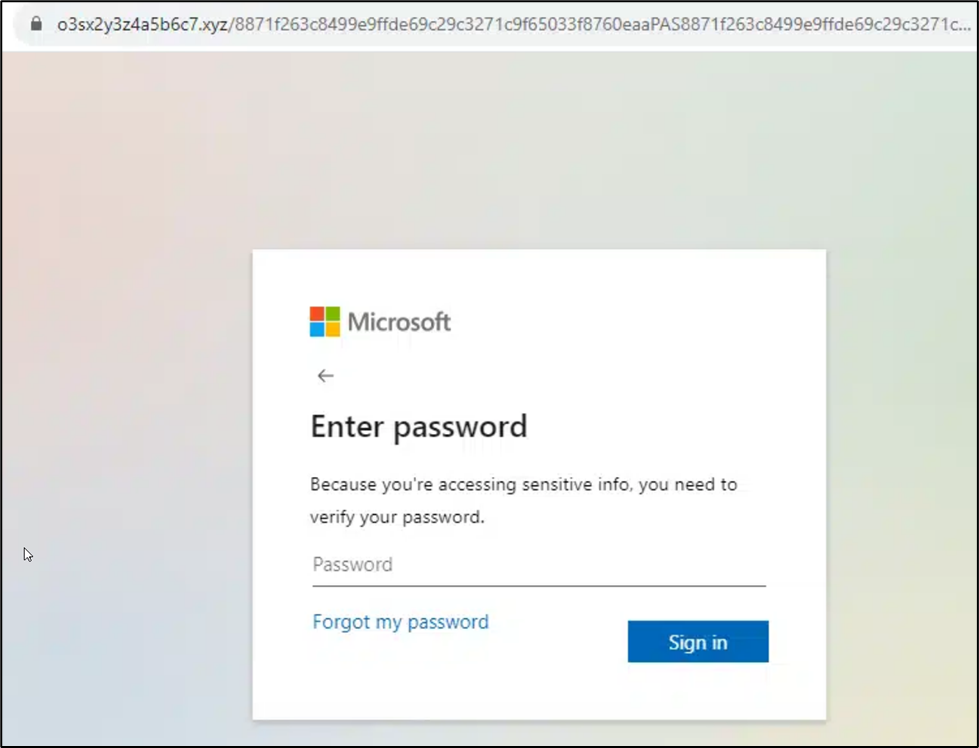
Image 2: Final phishing website designed to obtain Microsoft credentials
Despite using the subdomains of well-known companies to mask the phishing link, the lure content in phishing emails we observed was not related to these companies. Rather, the threat actors chose to use generic social engineering techniques to entice the recipient into clicking the link.
Setting up this attack is simple in theory. First, the threat actors must identify an open redirect vulnerability (CWE-601) on a trusted website. A simple, yet time-consuming, way to do this is by searching for “inurl:rts/go2.aspx” which will return a list of sites running the script abused during this campaign.
Second, the threat actor must identify the parameter that specifies the next destination, replace it with the desired URL, and verify that the script will indeed re-direct visitors. If properly configured, the script should not redirect to a URL or resource external to the hosting website. Therefore, it takes trial and error using this method before a vulnerable redirect is found. Technically proficient hackers would likely develop and use a script to accelerate this process.
Conclusion
Fortunately, within 24 hours of Field Effect detecting this campaign, many of the redirects involved were no longer functioning. This is likely due to security controls detecting the traffic to external domains and making the necessary configuration changes to close the open redirect.
The effectiveness of a phishing campaign of this nature is two-fold. First, including the legitimate domain of a prominent company at the start of a URL is an effective way of tricking recipients into thinking the email is legitimate. Especially when the domain does not have an association with third-party data, as may be the case with file sharing or hosting websites. Second, it is possible that anti-virus software or email security products will not identify malicious domains when found as parameters in URLs of non-malicious domains.
Recommendations
Threat actors are constantly looking for infrastructure that can be used to support their malicious activities. When that infrastructure belongs to popular and reputable companies, it’s even more effective. Field Effect recommends that companies ensure internet-exposed resources like redirects, DNS resolvers, and proxies are properly configured so that they can only be used for their intended purpose.
Indicators of Compromise
christiesaustralia[.]au
clinicacoyoacan[.]com
treelite[.]com
viadocsviasigndocs[.]com
mudardevidaja[.]com[.]br
cireqld[.]com[.]au
o3sx2y3z4a5b6c7[.]xyz
xcczpt42u58vwkfjb2l7[.]c5qr[.]ru
