Two developers of information-stealing malware, known as infostealers, recently advertised a new capability to restore expired Google cookies, potentially allowing threat actors to bypass passwords and multi-factor authentication requirements to gain full persistent access to Google accounts.
The makers of the Lumma Infostealer advised on November 14 that its most recent update (version 13.11) added the ability to restore dead Google cookies using a key from restored files. The capability is only available to Corporate Plan subscribers. Not to be outdone, the makers of the Rhadamanthys infostealer quickly announced that they, too, had added the same capability.
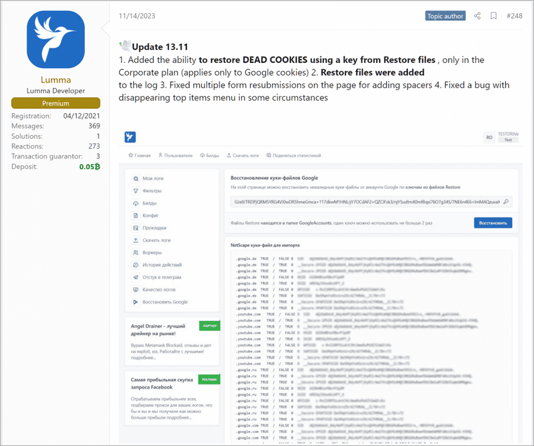
Image 1: Lumma's update with expired cookie restoration feature added
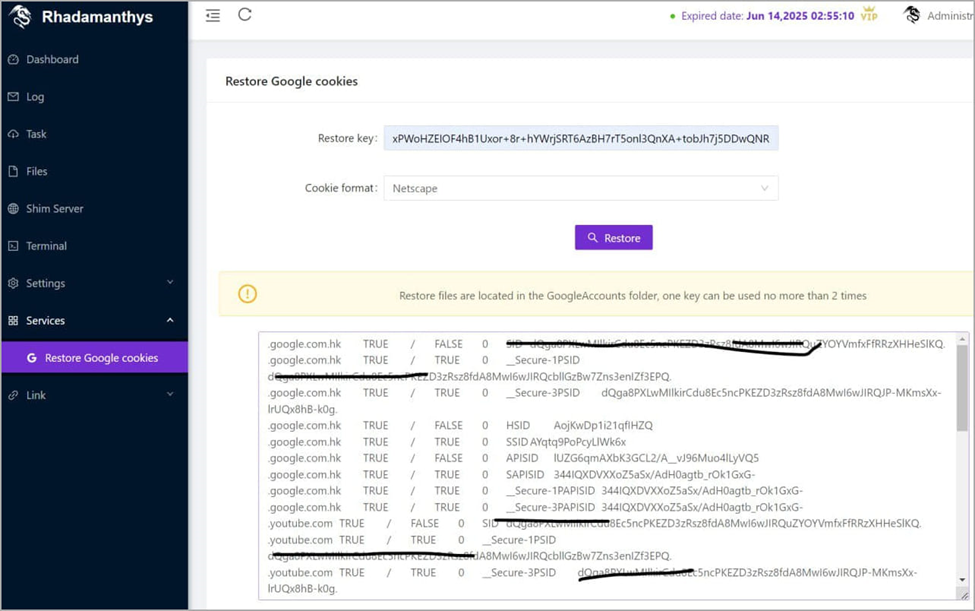
Image 2: Rhadamanthys' Google expired cookie restoration feature
Google has yet to comment on the issue, but the claim by at least two infostealers to possess the capability suggests Google’s cookie management process may have a zero-day vulnerability that threat actors have figured out a way to exploit.
Efforts to obtain more details on each infostealer’s cookie restoration process have been unsuccessful, as neither threat actor is willing to share specifics. However, Lumma’s representatives did not miss the opportunity to accuse Rhadamanthys of copying its idea.
Source: Bleeping Computer
Analysis
Preliminary research has revealed that there is some truth to Lumma and Rhadamanthys’ claims.
However, the research has also revealed at least one limitation to the exploit: the restored cookie may no longer work after the user resets their account’s password if the threat actor isn’t using a browser that adequately mimics the victim’s environment. Unfortunately, the average skilled threat actor would be using such a browser.
Mitigation
It’s very difficult for users to protect themselves from this threat until Google deploys a fix. Until then, the best way to mitigate the threat is to avoid downloading the infostealer malware in the first place.
In addition to adhering to security best practices, Field Effect recommends that users avoid downloading torrent files and executables from untrusted sources and sponsored ads in Google search results.
Related articles
