On May 31, Progress Software announced it had discovered a zero-day vulnerability in its MOVEit Transfer product that could lead to escalated privileges and potential unauthorized access to the IT environment.
The next day, Progress released a patch for all affected versions of the product and recommended users install it as soon as possible. Despite the quick turnaround between the discovery of the vulnerability and the release of a patch, threat actors were able to exploit this vulnerability, causing an unknown, but likely high, level of damage.
A golden opportunity for threat actors
The vulnerability, now designated CVE-2023-34362, is a SQL injection vulnerability that could allow an unauthenticated attacker to gain access to MOVEit Transfer's database, which in many cases contains personally identifiable and financial information, sensitive files, and other data requiring secure transfer.
A Shodan scan for MOVEit Transfer reveals that there are at least 2,534 instances of the product running worldwide while the majority (1,853) are in the US. A closer look at the specific organizations running the software is more concerning, and reads like a hacker’s wish list, with many organizations from the coveted financial, government, insurance, energy, telecommunications, defense, and education sectors included.
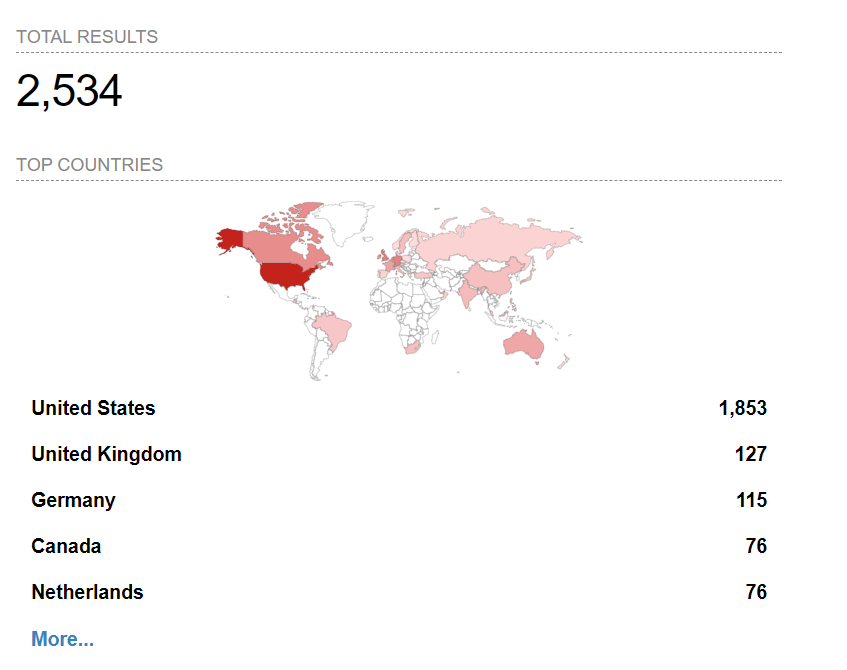
Image 1: Map of hosts running MOVEit Transfer (Source: Shodan.io)
The list of important organizations running MOVEit Transfer, coupled with the high likelihood of sensitive information stored within those instances, represents a golden opportunity for various threat actors—from nation-state groups seeking secrets to cybercrime groups looking to exploit personal and financial information.
Exploitation in the wild
Field Effect has already obtained evidence of probes for vulnerable MOVEit Transfer deployments in Covalence telemetry. Additionally, Mandiant recently reported that it had observed threat actors as early as May 27th using the vulnerability to deploy web shells and steal data.
Furthermore, it appears at least one ransomware group also likes to “move it, move it” (c’mon, I had to make a reference to Reel 2 Real’s 1993 smash hit!) Microsoft recently tweeted that it has linked attacks exploiting the MOVEit Transfer zero-day vulnerability to Lace Tempest, a threat group known for its ransomware operations, running the Clop extortion site, and using similar vulnerabilities in the past to steal data and extort victims. Although Lace Tempest appears to be the first ransomware gang to publicly claim a successful MOVEit Transfer attack, I’m sure it won’t be the last.
Notable victims of the vulnerability
Reports of MOVEit Transfer compromises are also emerging from victims themselves, with the BBC and British Airways among some of the big-name companies announcing they had been affected. Hitting a little closer to home for me, the Government of Nova Scotia recently announced that it too had been compromised, which resulted in the theft of social insurance numbers, addresses, and banking information of 100,000 current and former provincial employees.
Why isn’t the stolen data encrypted?
MOVEit Transfer markets itself as a secure data transfer solution with the ability to encrypt data at rest and in transit. So how then are threat actors able to steal useable, clear text data? Shouldn’t it be encrypted and therefore unusable? Progress has yet to provide answers to these questions, but according to this 2021 article posted in a MOVEit Transfer support forum, files are not encrypted when they are stored in the cache directory because this is where they may undergo different transformations with scripts before they are encrypted to be uploaded. Therefore, it’s plausible that threat actors are stealing unencrypted data from this directory.
Another possibility is that threat actors have been able to steal decryption keys directly from the database, and in turn, use them to decrypt the stolen encrypted data. The latest advisory from Progress indicates that “an attacker may be able to infer information about the structure and contents of the database in addition to executing SQL statements that alter or delete database elements via HTTP/HTTPS”. Perhaps “alter database elements” is a carefully crafted way to say data can be decrypted by using the right HTTP post. A scary thought for sure.
Field Effect continues to investigate the exact method hackers are using to obtain unencrypted data and will provide further updates as new information is obtained.
Update June 12 - On June 9, Progress announced that further code reviews helped uncover an additional SQL injection vulnerability that could potentially be used by a bad actor to stage an exploit. This new vulnerability, not yet assigned a CVE designation, is distinct from the previously reported vulnerability shared on May 31, 2023. According to Progress, the new vulnerability could allow an un-authenticated attacker to submit a specially crafted payload to a MOVEit Transfer application endpoint which could result in modification and disclosure of MOVEit database content. Unfortunately, Progress does not indicate if the content of the database is encrypted or not.
Conclusion
Secure data transfer services, such as MOVEit, will continue to remain popular targets for exploitation given the nature of the data they secure and the desirable list of organizations using them. Including MOVEit Transfer, four of the 10 most popular secure file transfer services have already been breached by threat actors, suggesting the pattern is likely to continue.
It’s incumbent on these vendors to ensure that their products are developed securely from the very beginning, and constantly tested and patched for vulnerabilities once released. If your organization is using a secure data transfer service, it's a good time to make sure proper mitigations are in place to detect unauthorized access, misconfigurations, and data theft before a vulnerability is officially announced.
Recommendations
- Apply the mitigation measures and patch any affected versions of MOVEit Transfer as soon as possible according to the instructions issued by Progress.
- Covalence users, ensure quick review of any AROs related to the detection of MOVEit Transfer software.
- Covalence users, submit suspicious email messages related to MOVEit Transfer to our Suspicious Email Analysis Service (SEAS). Threat actors often use popular breaches as the subject of phishing emails to increase their chances of success.
