Fresh off the heels of CISA advising that Fortinet’s FortiGuard routers were one of several types of routers being used by People’s Republic of China State-sponsored cyber actors to facilitate a campaign against Western critical infrastructure organizations, Fortinet once again finds itself in the headlines, this time regarding a newly discovered critical vulnerability.
Designated CVE-2023-27997, the vulnerability affects Fortinet devices with SSL-VPN components, and can allow remote code execution (RCE) without authentication, even if multi-factor authentication (MFA) is enabled.
About CVE-2023-27997
Fortinet is yet to make a formal statement regarding this vulnerability and there are few details regarding what threat actors can actually exploit with it. According to its discoverers, the vulnerability affects the remote web interface of FortiGate’s SSL-VPN component used by end-users, potentially allowing threat actors to interfere with the VPN.
Of note, this is a pre-authentication vulnerability, meaning the threat actor doesn’t need to be authenticated to take advantage of CVE-2023-27997—even if MFA is enabled.
The good news is that as far as we know, this vulnerability has only been discovered by ethical hackers who were careful not to release any information that would allow threat actors to take advantage of this vulnerability before a patch was developed, which Fortinet released on June 9.
However, due to the popularity of Fortinet devices (see below) and the fact that the exploit doesn’t require authentication, it’s likely only a matter of time before eager threat actors reverse engineer the patch and figure out how to target non-patched appliances.
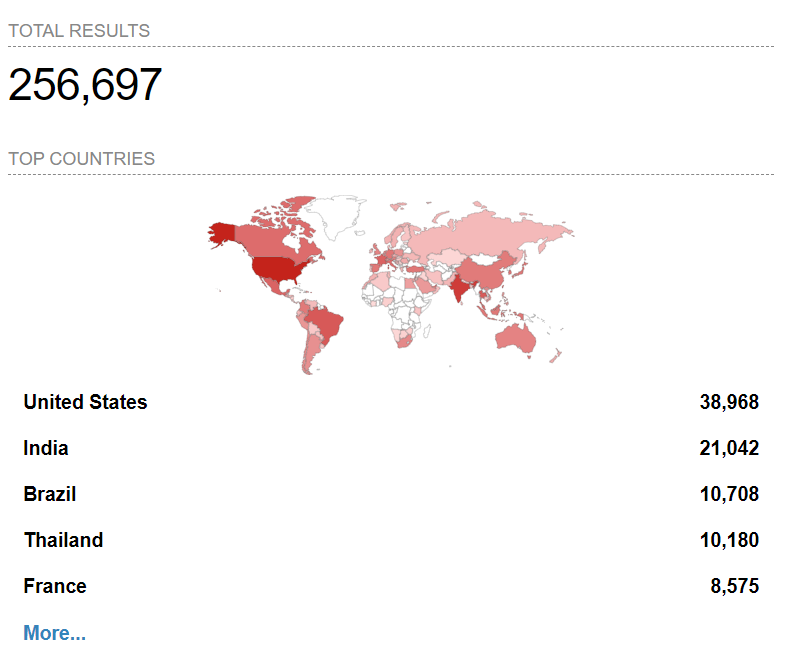
Shodan scan for FortiGate appliances. (Source: Shodan.io)
Update June 13: Fortinet now says that CVE-2023-27997, described as a heap buffer overflow in SSL-VPN pre-authentication vulnerability, may have been exploited in a limited number of cases. However, Fortinet stopped short of linking the vulnerability to recent Volt Typhoon (People’s Republic of China threat actor) activity, instead indicating that Volt Typhoon likely relied on a different Fortinet vulnerability, CVE-2022-40684, for initial access. Although Fortinet isn’t linking CVE-2023-27997 to Volt Typhoon at this time, it expects that all threat actors, including Volt Typhoon, will continue to exploit unpatched vulnerabilities in widely used software and devices, and urges users to patch affected systems as soon as possible.
Conclusion
Organizations using VPN services should take care to do their homework before choosing a vendor, including examining their history of vulnerabilities and patching cadence. This vulnerability serves as a great reminder that MFA isn’t the holy grail of cyber defense, but just one of many tools that should be deployed as a layered and overlapping defense.
Recommendations
If your organization is running the vulnerable versions 6.0.17, 6.2.15, 6.4.13, 7.0.12, or 7.2.5 of Fortinet’s FortiGate SSL VPN appliance, install the patch as soon as possible according to Fortinet’s instructions.
As for Covalence users, Covalence automatically scans and reports on vulnerable devices, software, and firmware within environments. Please ensure a quick review of any AROs you may receive regarding the detection of vulnerable FortiGate appliances.
