Threat actors are leveraging the global outage caused by a flawed update deployed to CrowdStrike’s Falcon sensor to target organizations with malware. Several cybersecurity researchers and agencies have reported observing an uptick in CrowdStrike-related phishing emails, including one that offered a fictitious Hotfix update that installed a remote access tool (RAT) known as Remcos.
Threat actors were also observed distributing a data wiper via the typo-squatted domain ‘crowdstrike.com[.]vc’. Once installed by a user expecting a CrowdStrike update, the wiper overwrites every file with zero bytes and then brags about it in a post on Telegram. The pro-Iranian hacktivist group Handala took credit for this campaign, stating that their goal was to target Israeli companies.
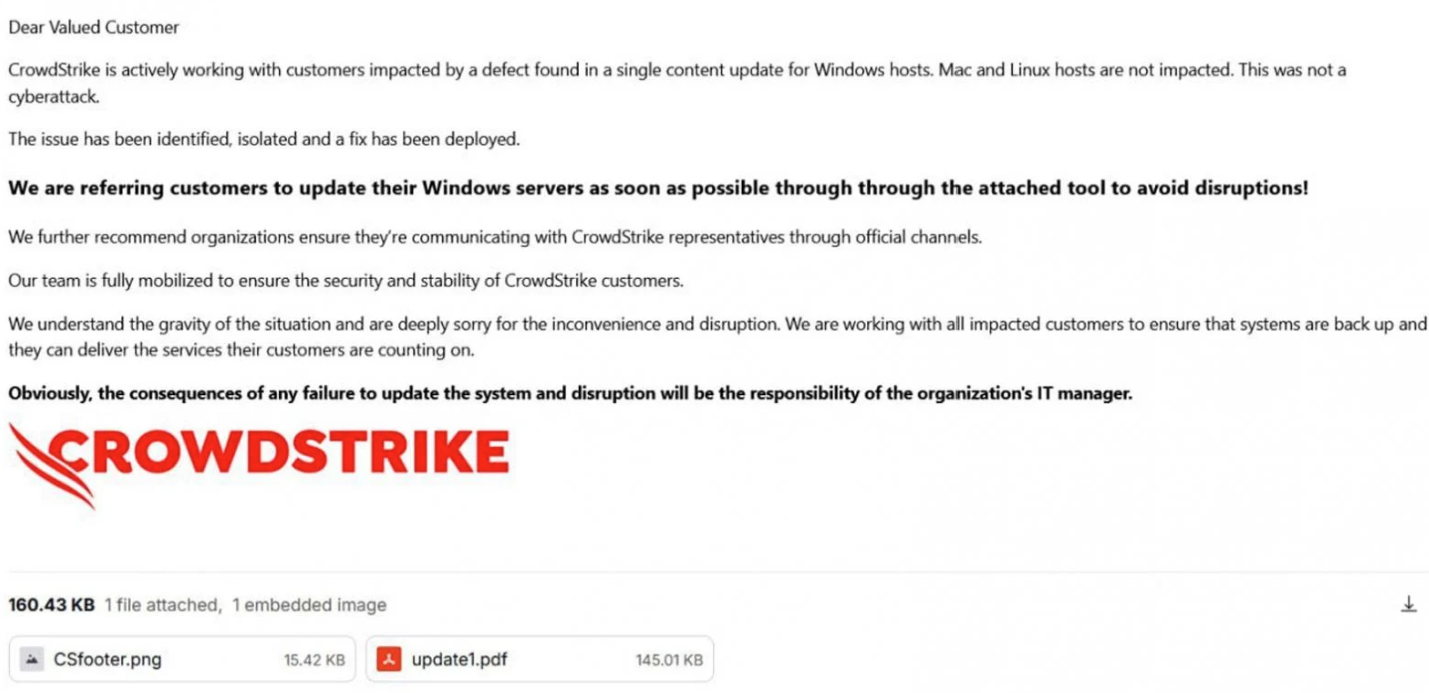
Image 1: Phishing email used by Handala
CrowdStrike has acknowledged that threat actors are exploiting the situation and has advised its customers to ensure that they are communicating with official CrowdStrike representatives through official channels.
Source: Bleeping Computer
Analysis
It’s not uncommon for threat actors to take advantage of major breaches by contacting likely customers of the affected software. Posing as an employee trying to help the customer, the threat actor’s true purpose for the call is to gain unauthorized access they can use to steal data or deploy malware. The method has a higher chance of success since the potential victim may be expecting a call from the provider and is motivated to fix the issue in question.
This type of activity was recently observed after the car dealership software CDK Global suffered an outage due to a ransomware attack, forcing thousands of car dealerships to use pen and paper to carry out operations for several days.
So far, Field Effect hasn’t observed any CrowdStrike-themed attacks within our telemetry, however, we continue to monitor the situation.
Mitigation
Field Effect recommends that CrowdStrike customers who are still impacted by the faulty update adhere to the official advice provided by CrowdStrike in its latest advisory. Additionally, Microsoft has released a custom recovery tool that automates the removal of the problem CrowdStrike update from Windows devices so that they can once again boot normally. It can be found here.
Related Articles
