SonicWall has released emergency patches for 15 security flaws discovered in its Global Management System (GMS) and Analytics, the company’s network reporting engine. The responsibly disclosed bugs include four critical vulnerabilities that can be exploited remotely by unauthenticated threat actors in unsophisticated attacks that don't require user interaction.
A successful exploitation could allow an attacker to access, steal, manipulate, or delete data found on the compromised system.
SonicWall has not detected active exploitation of the vulnerabilities in the wild nor has it observed the availability of proof of concept (PoC) exploit code. Regardless, SonicWall is urging its customers to upgrade to patched versions as soon as possible.
Source: Bleeping Computer
Analysis
SonicWall’s large product suite is deployed widely throughout the world (see below) and has a history of being exploited by cybercriminals and nation-state actors alike.
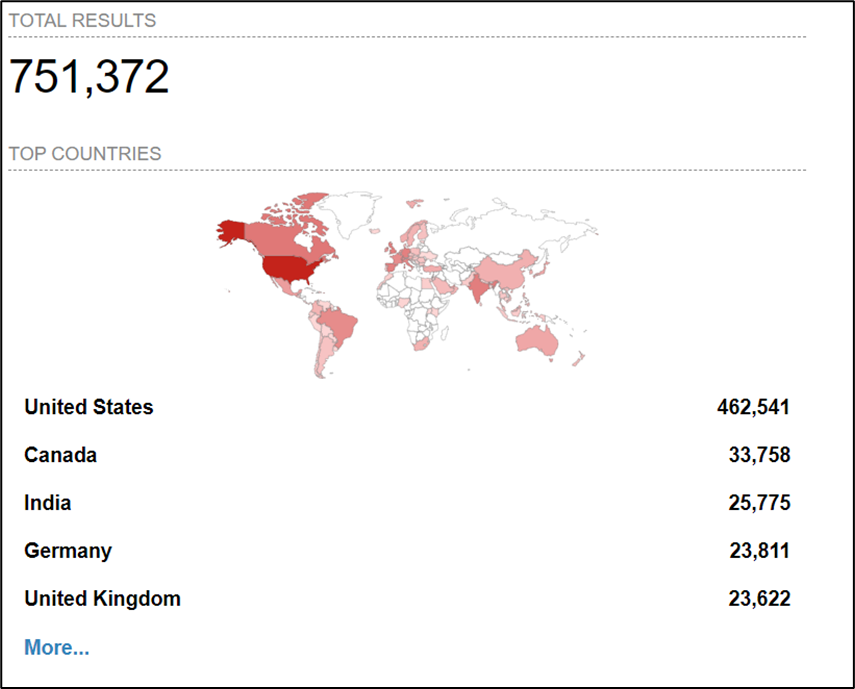 Image 1. Scan results for SonicWall devices. (Source: Shodan.io)
Image 1. Scan results for SonicWall devices. (Source: Shodan.io)
For example, in March 2023, suspected Chinese hackers gained long-term access to unpatched SonicWall Secure Mobile Access (SMA) appliances by installing custom malware. This same vulnerability was also exploited by HelloKitty and FiveHands ransomware groups in April 2023.
The responsible disclosure of unpatched vulnerabilities is critical to ensuring network defenders stay one step ahead of threat actors. Had researchers not discovered this vulnerability, it would likely only be a matter of time before it was developed and deployed by threat actors for malicious purposes. However, now that a patch has been released, it’s possible that a motivated threat actor will attempt to reverse engineer the patch to develop exploit code to target unpatched systems.
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities discovered in devices and software like SonicWall. This research contributes to the timely deployment of signatures into Covalence to detect and mitigate the exploitation of these vulnerabilities. Covalence users are automatically notified when vulnerable software and devices are detected in their environment and are encouraged to review these AROs as quickly as possible.
Field Effect strongly encourages users of SonicWall devices to update to the latest version soon as possible.
References
