VMware has advised that threat actors are currently exploiting a three-month-old vulnerability in its vCenter Server management platform for VMware vSphere environments used to manage ESX, ESXi, and virtual machines.
CVE-2023-34048, an out-of-bounds write vulnerability that was patched in October 2023, can be remotely exploited without authentication or user interaction, potentially leading to the exfiltration of data and/or the deployment of malware such as ransomware.
VMware servers are a popular target for brokers who sell access to compromised servers on cybercrime marketplaces. Ransomware and cybercriminals then purchase this access and later encrypt and exfiltrate victim data to demand large ransoms.
VMware has urged users to install the latest security patch as soon as possible. In the meantime, users can restrict network access to all management components and interfaces in vSphere, specifically ports 2021, 2014, and 2020, which have linked to exploitation activity. VMware has also released patches for unsupported versions of vCenter.
According to online scans, there are approximately 2,000 instances of VMware vCenter servers deployed throughout the world, with the majority located in the U.S.
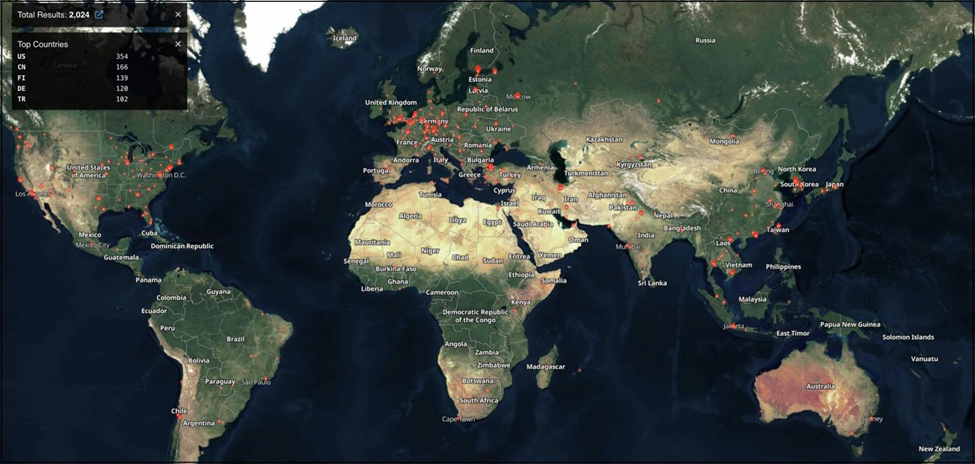
Scan results for VMware vCenter Servers (Source: Shodan.io)
Source: Bleeping Computer
Analysis
This campaign serves as a reminder of the importance of patching vulnerable systems as soon as possible, especially those with a history of being targeted by both criminal and state-sponsored threat actors.
In June 2023, VMware issued a similar warning to users of Aria Operations for Networks that the patched vulnerability CVE-2023-20887 had been exploited in the wild.
Fortunately, the footprint of affected vCenter servers (~2,000) is relatively small compared to the nearly 200,000 total VMware appliances deployed worldwide. This will likely deter some threat actors from purchasing or deploying exploits for CVE-2023-34048, choosing instead to exploit more widespread vulnerabilities.
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities discovered in software such as VMware. This research contributes to the timely deployment of signatures into Covalence to detect and mitigate the exploitation of these vulnerabilities.
Covalence users are automatically notified when vulnerable software is detected in their environment. Users can log in to your Covalence portal to review your AROs regularly.
Field Effect strongly encourages all users of VMware vCenter servers to install the latest security patch and take the necessary mitigation measures as soon as possible.
Related articles
