Phishing has always been a popular technique for threat actors, and 2023 was no exception. Fortunately, as part of the Covalence solution, users can submit suspicious emails they receive to our Suspicious Email Analysis Service (SEAS) which will provide them with details regarding any potential threat the email contains.
In 2023, we saw phishing methods continue their evolution and ongoing attempts to circumvent technical security measures and user awareness. These are the top 10 trends we have observed:
1. Increased layers of redirection
Almost all phishing links now use redirection, with one, two, or even more domains in the redirection chain. Furthermore, threat actors increased their use of legitimate services for the first domain in the chain, such as search engine links, or use browser redirection services provided by legitimate email marketing solutions.
Identify, measure, and reduce cyber risk with a personalized attack surface report.
Our automated attack surface reports detect end-of-life software and operating systems, exposed devices and services, third-party risks & more.
Try it free
This technique invalidates most IoC-based solutions and detections, since these solutions only monitor the first hop rather than the complete redirection chain. It also has the added benefit of allowing phishing links to remain valid for longer, as subsequent links in the redirection chain can be swapped out post-email delivery if any of them get blocked.
2. QR code phishing
QR code phishing has surged as a delivery method. This technique poses a double threat as QR code phishing can move click-through network traffic to a separate device (e.g., personal mobile), and potentially even another network (e.g., mobile carrier), making it much harder for network defenders to block and conduct investigations in the case of successful phishing incidents.

Example of QR code phishing spoofing Adobe.

Example of QR code phishing spoofing Microsoft.
3. Evolving financial redirection tactics
Financial redirection attacks via phishing have evolved this year. Historically, financial redirection has targeted payments to/from clients and vendors. However, in 2023, Field Effect observed a trend toward payroll-based financial redirection.
In this scenario, the attacker impersonates an internal employee and sends an email to the company’s finance team requesting a change to their payroll deposit information. The new details lead to an account under the threat actor’s control.
4. Use of anti-automated scanning services
Almost all effective phishing landing pages now use Cloudflare or similar services to protect them from automated scanning. This tactic allows the threat actor to leave landing pages online longer, usually for a few days rather than hours when this technique isn’t used.
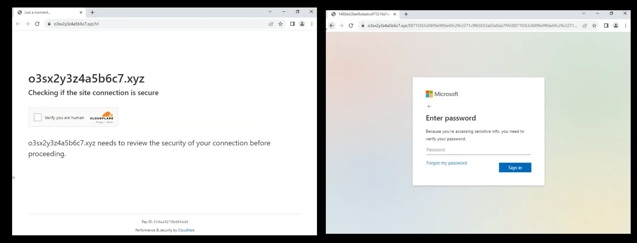
Example of using an anti-DDoS service to protect phishing pages from automatic scanning.
5. JavaScript obfuscation
Field Effect has observed several phishing pages that also use JavaScript obfuscation on the page source code. This technique makes it difficult for automated scanners and analysts to rule out the delivery of secondary payloads.
6. Images with text
The use of images with text, instead of just raw text, now seems to be the go-to delivery method of social engineering prompts on high-volume phishing campaigns. This is done to bypass text-based filters. In the more advanced cases, the social engineering prompt is broken up across several images to confuse Optical Character Recognition (OCR) scanners.
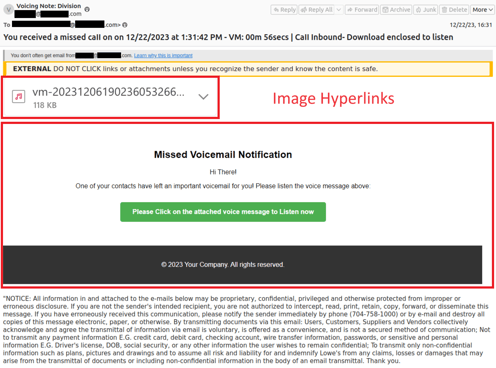
Example of using images of text rather than plain text.
7. HTML smuggling relying on JavaScript obfuscation
HTML smuggling is dropping off in prevalence. When the tactic does show up, it often relies on heavy JavaScript obfuscation or cipher texts to bypass filtering (these are decrypted when the HTML is opened, and the JavaScript is executed).
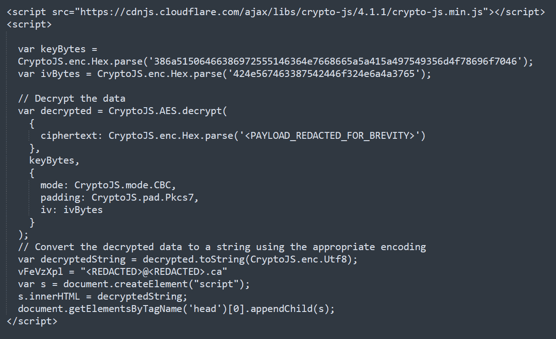
Example of JavaScript obfuscation within HTML smuggling technique.
8. Indirect targeting
Threat actors have developed new approaches to targeted spear phishing, such as indirect targeting. For example, Field Effect has observed threat actors weaponizing email chains stolen from previously compromised accounts and sending them to third-party targets.
This tactic gives the appearance that the target was accidentally added to an email chain in which sensitive information was being shared, providing a ruse to include a link or a file.
The perceived legitimacy and the apparent possibility of accessing sensitive information makes it extremely tempting for the target to open the link or attachment even if they believe they are not the "intended" recipient.
9. URL obfuscation
Field Effect observed an increase in threat actors stretching the limits of what is considered a legitimate URL to confuse parsers. These URLs are technically valid but are not in a common or expected format, such as containing unusual characters or symbols. Less robust URL parsers will not accept or even detect these strings as URLs.
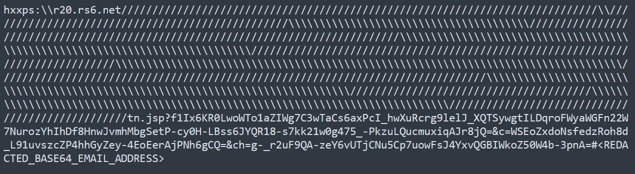
Example of uncommon URL format.
10. Combinations of tactics
Overall, combinations of the above trends are very common now. For example, a QR code image that delivers a phishing link which redirects through two domains, including a legitimate browser redirection service, before reaching a Cloudflare-protected phishing page.
What wasn’t observed:
Field Effect has observed limited instances of phishing attacks using trojanized PowerPoint, Word, or Excel documents with malware embedded in them. Additionally, Field Effect did not observe a substantial amount of phishing/malware delivery via third-party hosting and file sharing (Dropbox, Google Drive, OneNote, SharePoint, etc.)
The bottom line
Regardless of how many technical defenses an organization may have to detect and prevent phishing, it often comes down to whether the human recipient of the email is tricked into clicking a link, opening an attachment, or more recently, scanning a QR code.
As such, phishing awareness training and phishing simulations are effective tools organizations can use to reduce the risk of phishing as its complexity and breadth continue to evolve.
With heightened awareness and access to Covalence’s Suspicious Email Analysis Service (SEAS) for expert analysis and guidance, organizations can better defend against phishing, spear phishing, and other email-based cybersecurity threats.
