The Microsoft threat intelligence team (MSTIC), in collaboration with Ukraine’s Computer Emergency Response Team (CERT-UA), is reporting that the Russian Federal Security Service (FSB)-linked group, Turla, has targeted the defense sector of Ukraine and Eastern Europe with a novel .NET-based backdoor called DeliveryCheck.
DeliveryCheck is spread via spear phishing emails as attached documents with malicious macros. It establishes persistence by creating a scheduled task that downloads and executes the malware in memory. The malware then establishes a connection to a command and control (C2) server to retrieve further instructions, which include launching additional payloads from the embedded macros. The main objective of the attacks was to exfiltrate messages from the Signal messaging app for Windows to obtain sensitive conversations, documents, and images on targeted systems.
DeliveryCheck also has the ability to compromise Microsoft Exchange servers using PowerShell Desired State Configuration (DSC), a native PowerShell management platform that allows administrators to automate system configurations, effectively turning a legitimate server into a malware C2 server.
Source: The Hacker News
Analysis
The deployment of novel malware specifically developed to steal Signal messages was likely designed to fill a Russian intelligence gap related to the information being exchanged by Ukraine and its allies over the platform.
Russian state-sponsored cyber actors have a long history of targeting Ukraine with spear phishing messages with attached documents containing malicious macros. For example, in 2015, Russian Military Intelligence Directorate (GRU) hackers compromised several Ukrainian power companies using this tactic that eventually led to the disruption of power to nearly 200,000 homes.
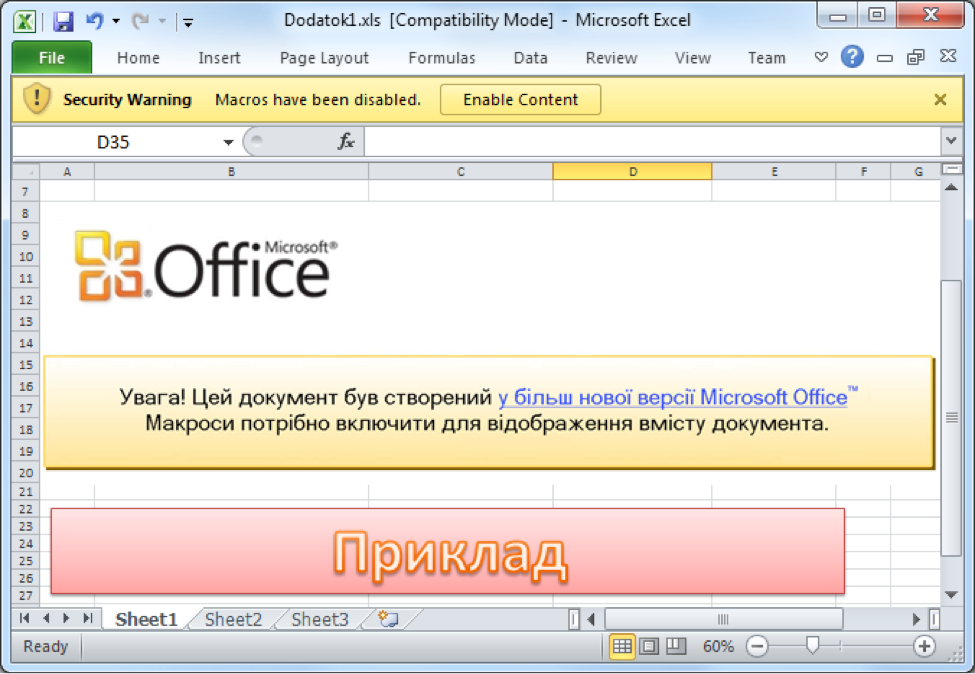 Screenshot of a malicious macro-enabled spreadsheet used by GRU hackers in 2015.
Screenshot of a malicious macro-enabled spreadsheet used by GRU hackers in 2015.
Russia is a very capable cyber actor that will continue to evolve its tactics, techniques, and procedures (TTPs) to satisfy its intelligence requirements on Ukrainian military, political, and strategic entities, for the duration of its invasion of Ukraine.
Mitigation
Field Effect recommends that governments and organizations in Ukraine, and those in support of Ukraine, adopt a heightened security posture towards cybersecurity given the threat posed by Russian state-sponsored cyber actors such as Turla. We encourage all organizations to review the U.S. Cybersecurity & Infrastructure Security Agency (CISA) ShieldsUp program, which provides robust guidance for preparing, responding to, and mitigating the impacts of Russian state-sponsored cyberattacks.
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for novel TTPs and indicators of compromise (IoCs) associated with nation-state-sponsored groups such as Turla. This research contributes to the timely deployment of signatures into Covalence to detect and mitigate threat activity. Covalence users are automatically notified when state-sponsored threat activity is detected in their environment and are encouraged to review these AROs as quickly as possible.
Field Effect recommends that organizations consider disabling the macro function of Microsoft Office files should it cause no impact on business operations.
References
