Earlier this month Google launched eight new top-level domains (TLDs) which can be purchased by anyone for websites and email servers. The new TLDs are: .dad, .esq, .prof, .phd, .nexus, .foo, .zip, and .mov.
The introduction of new TLDs is generally a good thing because it allows website owners to choose a TLD that better reflects the nature of the site’s content and purpose. However, the introduction of new TLDs also presents several threats, especially when two of them are also the extensions of files frequently shared online, .zip and .mov.
Get threat intel delivered straight to your inbox
The Field Effect Newsletter
The threat
When new TLDs become available, it allows threat actors to register what can appear to be legitimate domain names and create websites to support phishing campaigns and watering hole attacks using them. For example, a threat actor can mirror the website found at “domain.com” and upload it to their own “domain.phd”. Unsuspecting users, thinking they are looking at the legitimate domain.com website, can find themselves on the impostor website, leaving them exposed to browser-based exploits, malicious downloads, or other attacks. This threat is nothing new and surfaces every time a new TLD is introduced. Most security-conscious organizations have a process in place to register their domains with new TLDs to mitigate this risk.
The bigger issue is the potential misuse of the .zip and .mov TLDs since these TLDs are the same as popular file name extensions commonly found online. These TLDs have been around since 2014, however, it was not until May that they could be purchased by anyone for any purpose.
The main worry with the .zip and .mov TLDs is that some browsers, email clients, social media sites, and messaging platforms will automatically convert file names with those extensions to URLs. For example, instructions for a user to “unzip the update.zip file in ProgramFiles and launch the video.mov file” would now appear as “unzip the update.zip file in ProgramFiles and launch the video.mov file”. Since people are accustomed to finding the files they are looking for via the hyperlinked file name, they are inclined to click the link. The theory is that threat actors will register domains reflecting commonly used filenames and place a malicious file at the end of the URL.
There is also a way to make a file hosted on a malicious .zip and .mov TLD, or any TLD for that matter, appear as if it is hosted on a different legitimate site. Researcher Bobby Rauch discovered that with the clever use of the @ operator and Unicode character ∕ (U+2215), a threat actor can design an extremely convincing URL. For example, the URL https://github.com∕kubernetes∕kubernetes∕archive∕refs∕tags∕@v1271[.]zip appears to serve as a legitimate file from GitHub when it actually takes users to https://v1271[.]zip. This is because most browsers ignore everything before the @ character in a URL when combined with U+2215 slashes. This URL crafting trick will make it even more difficult for humans to spot dangerous links and reinforces the importance of both good user awareness and technical protections.
Examples in the wild
Popular .zip archive names have already been registered. Fortunately, it appears that many were registered by cyber security researchers attempting to beat threat actors to the punch. For example, the domain officeupdate.zip redirects to the Twitter feed for VX-Underground, who now claim to be the proud owner of everyone’s “favorite initial access method”.
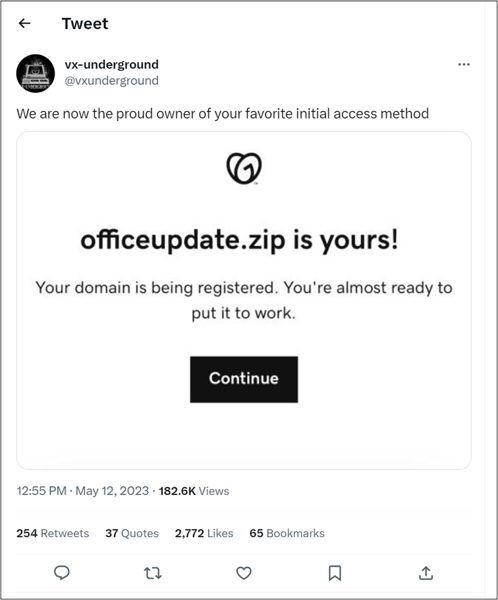
Image 1: Redirect of officeupdate.zip to VX-Underground’s Twitter feed. (Source: Twitter)
Field Effect has also identified newly registered .zip domains in our own telemetry, including financialstatement.zip and anyword.zip which appear to be registered to prevent misuse. The domain anyword.zip redirects to Swift on Security’s Twitter feed while the domain financialstatement.zip displays the website below:
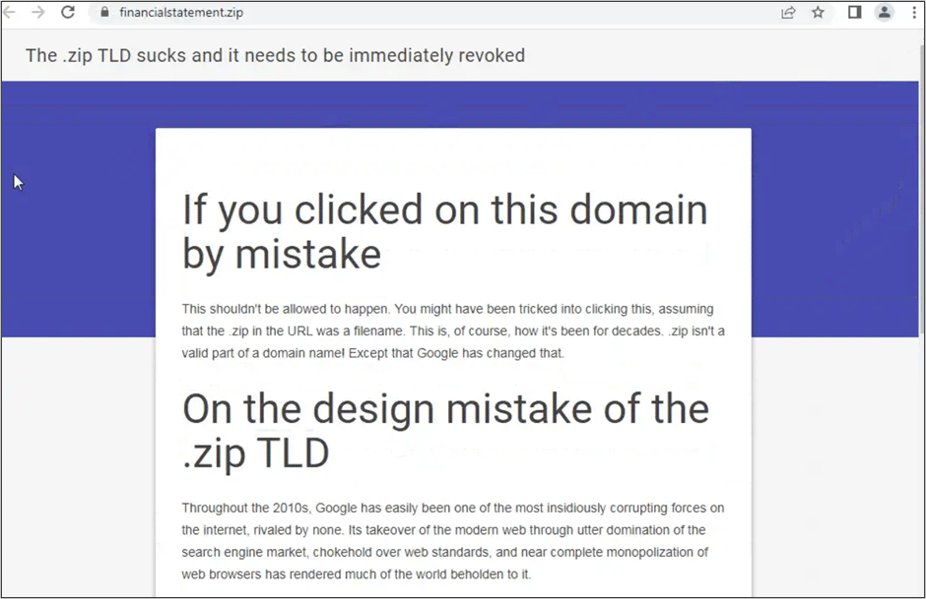
Image 2: Page displayed at URL financialstatement.zip. (Source: financialstatement.zip)
There have also been reports of .zip domains being registered to facilitate the theft of Microsoft account credentials. Silent Push Labs recently discovered the domains microsoft-office.zip and microsoft-office365.zip, both hosted on IP address 151.80.119.102. When visited, these sites displayed what appeared to be a legitimate Microsoft sign-in page, likely designed to capture credentials from unsuspecting visitors.
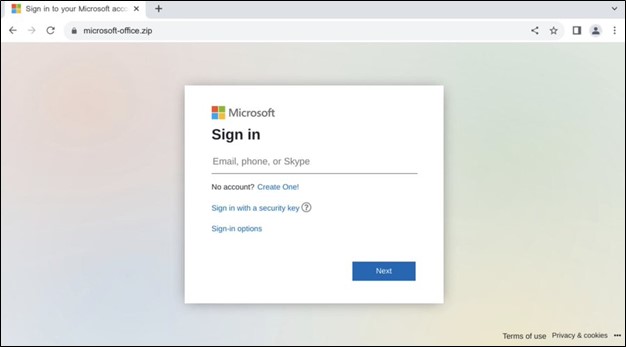
Image 3: Fake sign-in site found at Microsoft-office.zip and Microsoft-office365.zip. (Source: Silent Push Labs Twitter)
Conclusion
The cyber security community has been abuzz with debate on whether the new TLDs represent a legitimate concern, or if the risk is overhyped. There has also been much discussion on whether the Internet Corporation for Assigned Names and Numbers (ICANN) should have allowed these TLDs, and Google’s decision to make them universally available. However, now that the cat is out of the bag, it is very unlikely to be put back in, and thus time to begin considering the adoption of controls to mitigate the potential risk these TLDs pose.
Covalence users already have the benefit of our DNS Firewall which will proactively block malicious domains, our Domain Monitoring Service which will alert you to suspicious domain registrations that could be a risk to your organization, and of course, our Endpoint Monitoring which will protect your systems from attack.

Want to see Covalence in action?
Watch now
Recommendations
- Monitor for imposter or typo-squatted domains regardless of TLD. Block any that are found and action suspicious domains to anti-phishing authorities. (Covalence subscribers are automatically alerted when the registration of a suspicious domain is detected.)
- Proactively register your domain name for all available TLDs to reduce the chances threat actors will use them for malicious purposes. Redirect traffic from the secondary TLDs to ensure visitors reach the appropriate site.
- Configure applications to not automatically covert files with .zip and .mov extensions to URLs.
- Remind users to scrutinize any link before clicking on it and refrain from downloading files from untrusted sites.
- Covalence users, ensure quick review of any AROs related to the detection of connections to domains associated with malicious activities, regardless of their TLDs.
- Covalence users, submit suspicious email messages to our Suspicious Email Analysis Service (SEAS).
