Palo Alto Networks has issued a warning to users that a maximum-severity flaw affecting PAN-OS software used by its GlobalProtect gateways and portals is being actively exploited in the wild.
The vulnerability, designated CVE-2024-3400, is a command injection vulnerability in specific PAN-OS software versions (< 11.1.2-h3, < 11.0.4-h1, < 10.2.9-h1) configured for both GlobalProtect gateway and device telemetry. Successful exploitation of the vulnerability could allow an unauthenticated threat actor to execute arbitrary code with root privileges on the appliance.
Palo Alto expects to release a security update for the affected software on April 14, 2024. Until then, the company has advised users with a Threat Prevention subscription to enable Threat ID 95187 to mitigate the threat.
Source: The Hacker News
Analysis
Edge devices such as firewalls and gateways are popular targets for threat actors seeking initial access to targets of interest. Control of these devices could allow threat actors to obtain credentials that could be used to gain access to more sensitive systems and accounts or as a platform to launch adversary-in-the-middle attacks.
It’s likely that Palo Alto Networks would have preferred not to disclose the vulnerability until a patch was available, but was forced into issuing a warning when active exploitation was observed.
Unfortunately, it’s unknown for how long, and to what extent, threat actors have been exploiting this particular vulnerability. According to the Shadowserver Foundation, approximately 90,000 instances of GlobalProtect are deployed worldwide, with the majority (~55,000) located in the United States.
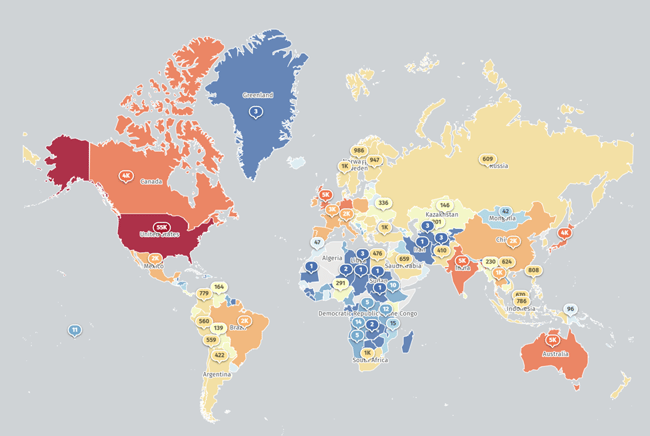
Image 1: Palo Alto GlobalProtect instances worldwide (Source: Shadowserver Foundation)
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities discovered in firewalls including Palo Alto’s GlobalProtect. This research contributes to the timely deployment of signatures into Covalence to detect and mitigate the exploitation of these vulnerabilities. Covalence users were automatically notified if any potentially vulnerable GlobalProtect gateways or portals were detected in their environment and are encouraged to review these AROs as quickly as possible via the Covalence portal.
Field Effect strongly encourages Palo Alto customers with a Threat Prevention subscription to enable Threat ID 95187 as soon as possible, as per the advisory. All other users should consider disabling any affected Palo Alto appliances until a patch is available.
Related Articles
