This is a guest post from Tari Schreider, C|CISO, CRISC, MCRP, and Strategic Advisor at Aite-Novarica Group.
Since Windows 7 was released on October 22, 2009, there have been 17 Windows versions released through May 2021. These included starter, basic, premium, professional, and enterprise versions installed on over one billion machines. The zero-day vulnerabilities found by Field Effect could have egregiously affected Windows machines across universities, hospitals, SMBs, governments, large enterprises, and critical infrastructures without discriminating by industry or geography. For fourteen years, the vulnerabilities discovered by the Field Effect security researchers have been lying dormant, waiting for a hacker to exploit the weaknesses in the Windows operating system. Unlike many zero-days that are discovered after an attack, these zero-days were discovered by the good guys before bad actors realized they existed. So why didn’t hackers find this zero-day first? It is a great question with no easy answer. Some might say they were preoccupied with launching ransomware; others may say they were too obscure to find. I say there are just too many zero-days in the wild and not enough security researchers to go around resulting in some remaining dormant forever.
The Rand Corporation (Rand) performed groundbreaking research in 2017, that although dated, holds to this day. Rand found the life expectancy of a zero-day was 6.9 years before they’re found by either the good or the bad guys. Rand further found the average time to develop a fully functional exploit was a median time of 22 days. No one knows how many zero-days are lurking in the code we use daily. Google’s Project Zero has tracked over 108,000 vulnerabilities since it was founded in July 2014. Over 200 of those vulnerabilities have been zero-day vulnerabilities. Project Zero also reports it takes on average 15 days to patch a vulnerability used in active attacks. If you like scary stories, check out Project Zero’s Oday “In the Wild” spreadsheet or skip it altogether if you’re faint of heart. There is no way to know how many cybersecurity researchers exist, or let alone hackers.
HackerOne claims over 300,000 hackers are available to look for vulnerabilities to earn a bounty. I choose to believe there are likely three times as many bad actors but a smaller contingent of highly sophisticated attackers with the means and resources to launch sophisticated attacks. Keeping zero-day vulnerabilities out of their hands is tantamount to protecting the world’s cyberinfrastructure and computing technology.
So, what would have happened if the bad guys got to these vulnerabilities before Field Effect discovered the tranche of seven zero-day vulnerabilities in April 2021? We could ask Alibaba, Facebook, LinkedIn, Marriott, and others that have all fallen victim to a zero-day attack how those attacks affected their business. The Third Annual Study on the State of Endpoint Security Risk from Ponemon Institute states that 80% of successful breaches result from zero-day exploits resulting in 538 organizations attacked. Let’s have a little fun and take some liberties with this data. If we assume the 80% attack rate, what would it look like if the zero-days found by Field Effect were discovered by the bad guys first? Yes, I know this isn’t very scientific, but it makes one think.
First, let’s give one of the Field Effect-found zero-days to seven groups of 538 organizations. Now let’s apply some attack and industry context. Figure 1 shows the types of attacks that could have been launched against these organizations using those zero-days.
The following figure looks at how those 3,766 organizations could have been attacked.
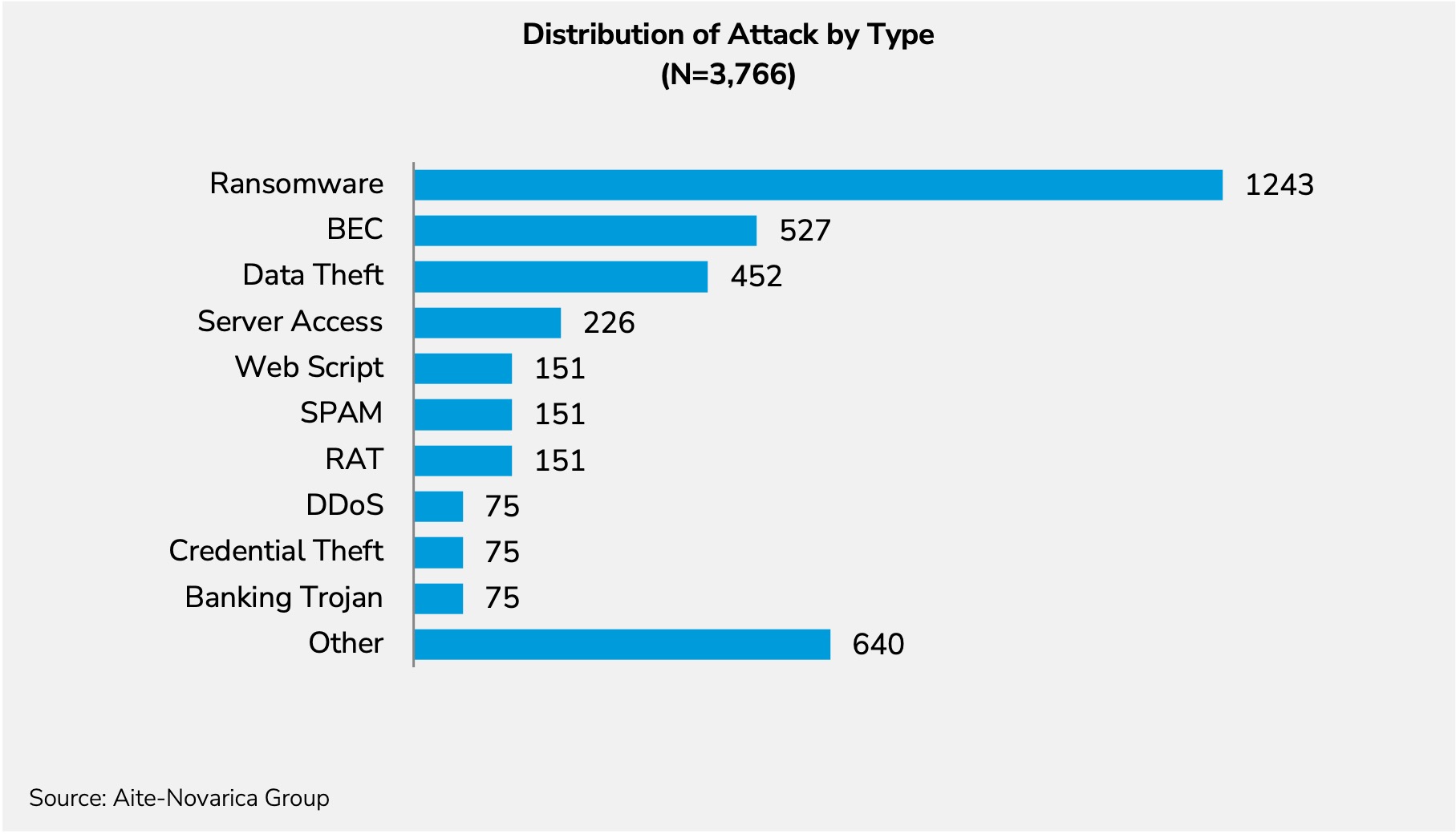
Figure 2 looks at the industries that could have been affected if the seven zero-days were exploited.
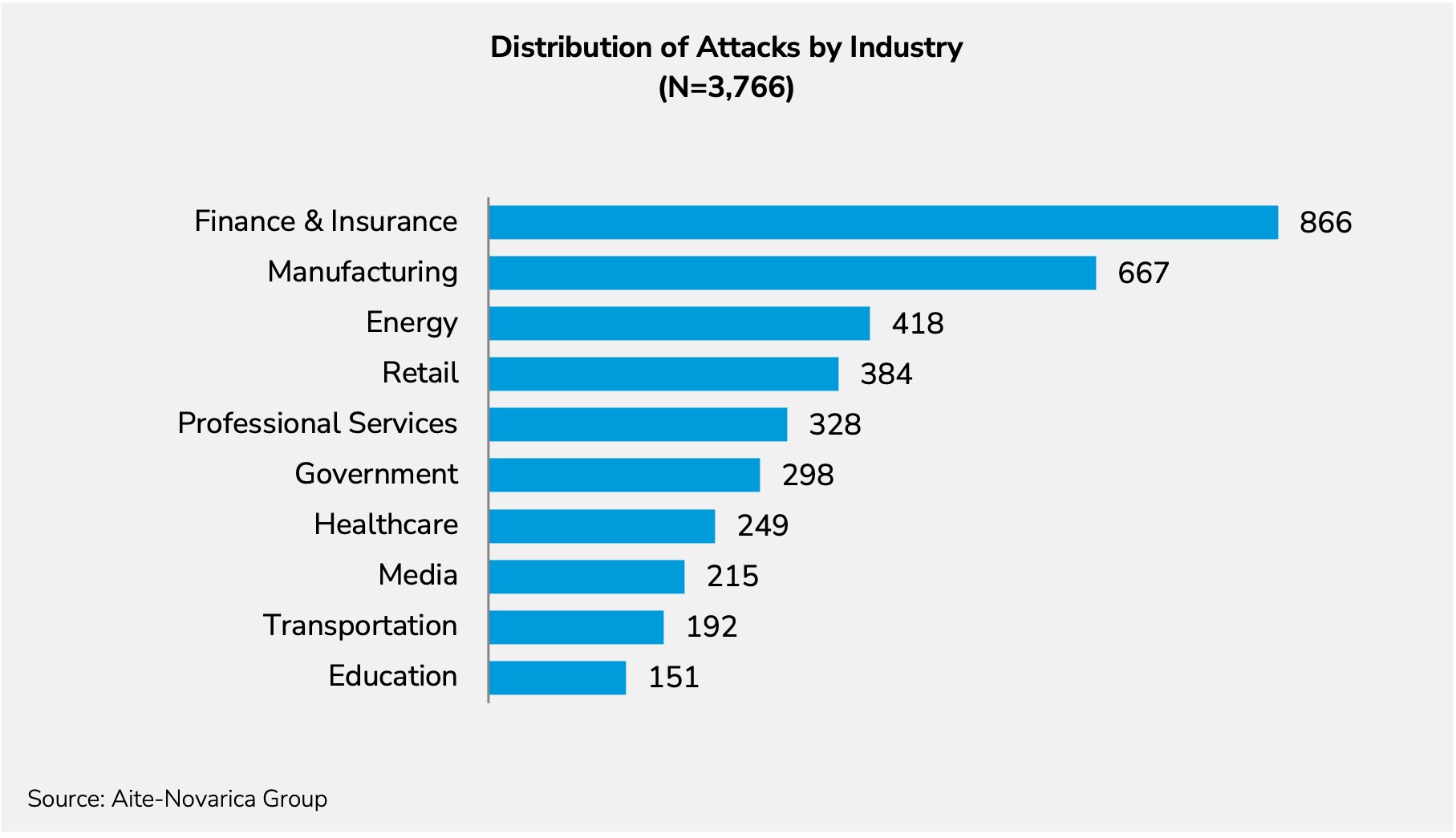
The distribution of attacks is drawn from the 2021 X-Force Intelligence Index for attack types in North America.
The average cost of a data breach in 2021, according to the Ponemon Institute report, is US$4.24 million. If all this held, the Field Effect zero-day Blackswan discovery potentially saved organizations over US$15.8 billion in losses. We always look at zero-days after they’re exploited, but we rarely look at the loss avoidance. Maybe it’s time to start an industry-wide initiative to track loss avoidance.
