At least two ransomware groups, Akira and Lockbit, have been observed conducting credential stuffing and brute-force attacks on Cisco Adaptive Security Appliances (ASA). The attacks make use of automated tools that conduct repeated attempts to log into the appliances using commonly used and default passwords. Successful exploitation leads to a foothold in the victim’s network from which further attacks can be launched, including the deployment of ransomware.
Fortunately, successful attacks appear to be limited to appliances that don’t use multifactor authentication (MFA), meaning the threat actors behind this campaign likely don’t have a method to defeat this security control.
Source: Bleeping Computer
Analysis
This campaign is a classic example of threat actors going after ‘low-hanging fruit.’ In this case, the targets are Cisco ASA VPNs exposed to the internet that use default or commonly used passwords that simple, automated tools can easily guess. This technique is not unique to Cisco devices and is essentially used on every internet-exposed device by threat actors looking for easy targets. This campaign also serves as a reminder of how effective MFA can be in thwarting threat actors’ malicious activities.
The apparent uptick in targeted Cisco ASAs could indicate that threat actors assume users of those devices have the means to pay ransom, or that threat actors have an unknown exploit they can use once they have access to further support their objectives.
According to Shodan, there are just over 300,000 Cisco ASAs deployed worldwide, with the majority residing in the US and China.
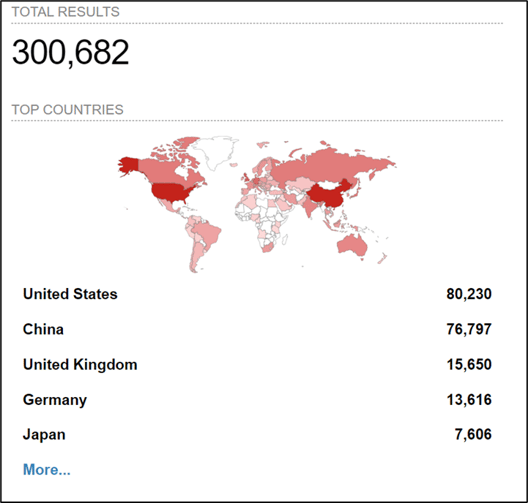
Scan results for Cisco ASAs. (Source: Shodan.io)
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for tactics like credential stuffing and brute-force attacks. This research contributes to the timely deployment of signatures into Covalence to detect and mitigate the exploitation of these vulnerabilities. Covalence users are automatically notified when these attacks are detected in their environment and are encouraged to review these AROs as quickly as possible.
Field Effect strongly encourages users to enable MFA on any internet-exposed appliance.
References
