JetBrains, the maker of the TeamCity continuous integration/continuous delivery (CI/CD) solution, is advising users of the on-premise version to upgrade to the latest version as soon as possible.
Updates are required to fix two vulnerabilities, originally discovered by a security researcher and reported to JetBrains in mid-February.
The flaws include CVE-2024-27198, a critical authentication bypass vulnerability and CVE-2024-27199, a path traversal vulnerability. Both vulnerabilities reside in the web component of TeamCity, impact all versions of on-premise instances, and could allow unauthenticated threat actors to remotely take control of exploited servers with administrative privileges.
Risk management made easy.
Pinpoint cybersecurity vulnerabilities and other risks to your business with a personalized attack surface report.
Get your ASR
According to technical details provided by the same researcher, CVE-2024-27198 can be exploited to create a new administrator account or generate a new administrator access token to get full control over the target server. CVE-2024-27199 is less severe, since it requires the threat actor to already be on the victim network, but could be exploited to conduct denial-of-service (DoS) attacks or to listen in on client connections.
Source: Bleeping Computer
Analysis
CI/CD solutions are used by developers to automate the development and testing of software products. Since these servers usually contain source code related to various projects, their compromise could lead to potential supply chain attacks if malicious code inserted by threat actors goes undetected and is subsequently installed by users.
A well-known example of this type of attack is the 2020 SolarWinds compromise, which was later attributed to Russia’s Foreign Intelligence Service (SVR), known as APT 29. APT 29 successfully penetrated SolarWinds' network in 2019 and used their access to insert a backdoor into a soon-to-be-released update for SolarWinds' Orion software. When users downloaded the update, they unknowingly installed the backdoor, which APT 29 later leveraged to exfiltrate data from targets of interest.
According to the Shadowserver Foundation, there are approximately 1,000 TeamCity deployments worldwide, with nearly 800 located in the US and Canada.
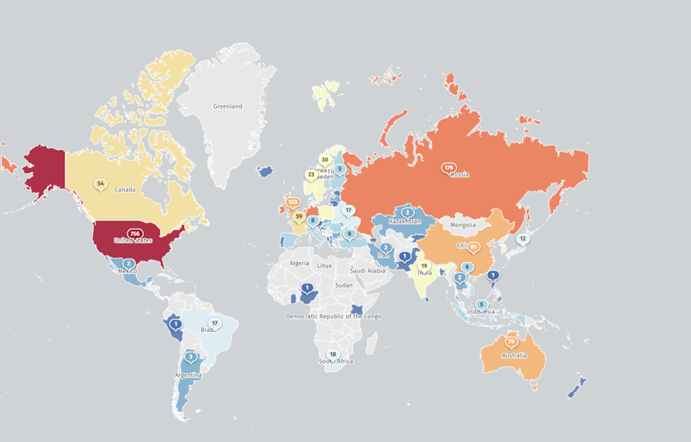
Image 1: Location and quantity of TeamCity deployments worldwide (Source: Shadowserver Foundation)
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities discovered in software like TeamCity. This research contributes to the timely deployment of signatures into Covalence to detect and mitigate the exploitation of these vulnerabilities. Covalence users were automatically notified via the Covalence portal if a vulnerable version of TeamCity was detected in their environment.
Field Effect strongly encourages all other users of affected on-premise TeamCity deployments to install the latest security patch as soon as possible per JetBrains' advisory.
Related articles
