Job seekers have become the victim of a cyber campaign, conducted by the North Korean state-sponsored cyber actors known as Lazarus, in which they are tricked into completing a coding test that contains malware.
Researchers believe this new attack vector is the continuation of Lazarus’s ‘VMConnect campaign’, which has been targeting software developers as early as August 2023 via spearphishing and trojanized job offer documents.
The attack begins when Lazarus approaches a target via LinkedIn, often posing as a recruiter from a prominent company such as Capital One. As part of the interview process, the unsuspecting candidate is asked to complete a coding exercise to prove their expertise in working with Python projects and GitHub, in this case, to find and fix a bug in a Python-based password manager application.
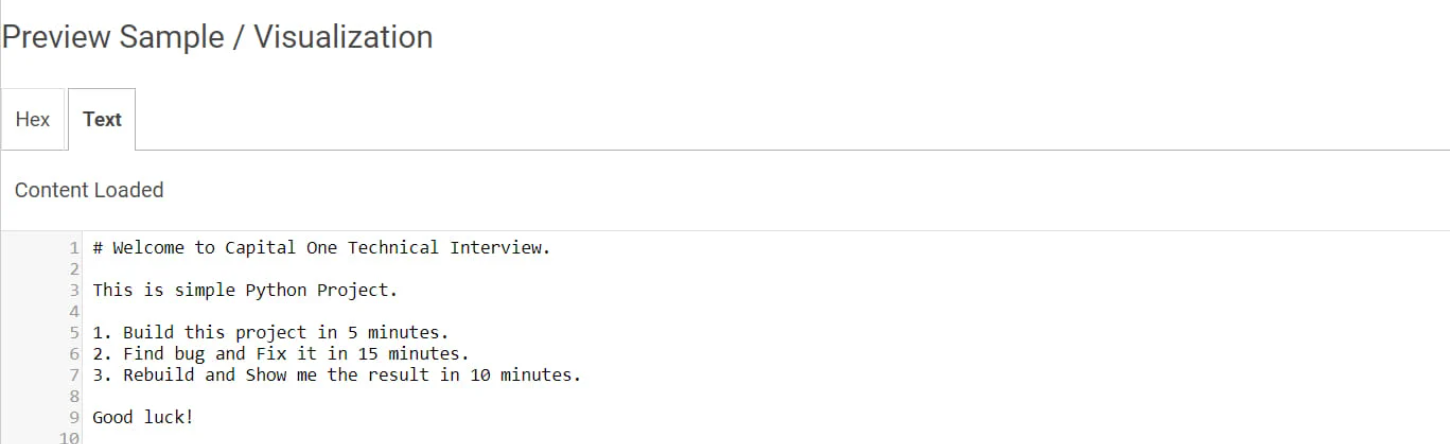
Image 1: Instructions for the code review exercise
The candidate is instructed to execute the application on their system before beginning their search for the bug, which is limited to 15 minutes. As a result of this tight time limit, the candidate is unlikely to notice a base64 obfuscated malware downloader hidden in the test files.
This downloader then establishes a connection with a command and control (C2) server and awaits further instructions.
Source: Bleeping Computer
Analysis
Lazarus is likely targeting software developers in hopes of gaining access to source code and other development projects the target may have knowledge of or access to. Should a target have used their company-issued laptop to take the test, Lazarus could theoretically access corporate code repositories and harvest credentials to enable unauthorized access to sensitive systems.
Stealing source code allows North Korea to stay competitive in a world in which sanctions prevent the country from acquiring the technology and skills required to support strategic programs like weapons and satellites. It also helps to identify vulnerabilities in code that could be leveraged as zero-days to enable future attacks.
Lazarus is known to use LinkedIn to identify and approach potential targets. Recently, the group used AI tooling to change one member's appearance during video interviews, duping cybersecurity company KnowBe4 into hiring the threat actor. Fortunately, the company caught on to the scam when the new employee installed malware on their company-issued laptop and contacted the FBI, who advised that the employee in question was a North Korean state-sponsored threat actor.
The FBI has issued warnings regarding North Korea’s use of this type of insider threat since 2022. According to the FBI, there have been multiple cases of North Korea-based IT employees who have successfully obscured their true identities and gained employment with Western companies. The revenue from these workers’ paychecks is then used to fund weapons programs and cyber operations, as well as to collect intelligence.
Mitigation
Field Effect’s Security Intelligence team constantly monitors the cyber threat landscape for threats from advanced cyber actors engaging in malicious activities, including Lazarus. This research contributes to the timely deployment of signatures into Field Effect MDR to detect and mitigate the risk these groups pose.
Field Effect MDR users are automatically notified when various types of malicious activities are detected in their environment and are encouraged to review these AROs as quickly as possible via the Field Effect Portal.
Field Effect recommends that software developers scrutinize job application invites via social media and take into consideration that the profiles contacting them could be fake. Additionally, efforts should be made to verify the recruiter’s identity and association with the company they claim to represent.
Finally, candidates should take the time to review test files carefully and only execute them in safe environments such as virtual machines or sandboxing applications.
Related Articles
