This blog is part of a series of posts highlighting how our flagship cybersecurity product, Field Effect MDR, can help our customers attain compliance goals.
Whether it’s to mitigate risks, maintain a cyber insurance policy, or fulfill a contractual requirement, we know how important it is for businesses to adhere to industry-standard compliance frameworks.
The good news is the right cybersecurity solutions can empower healthcare organizations like yours to achieve and maintain compliance with numerous frameworks, including the Health Insurance Portability and Accountability Act (HIPAA).
Securing healthcare information
HIPAA modernized the flow of healthcare information and stipulated how personally identifiable information maintained by the healthcare and health insurance industries should be protected from fraud and theft. HIPAA applies to most people and companies that use and access the Protected Health Information (PHI) of patients treated inside the USA, regardless of citizenship.
While HIPAA applies equally to physical records like medical charts, most healthcare clinics and organizations have adopted modern computing and digitized patient information into Electronic Protected Health Information (EPHI).
EPHI has revolutionized how you track and deliver care to patients, but has also opened sensitive data to a whole new range of threats, from malicious hackers to accidental disclosures. Regardless of size, your organization holds important client and organizational data that's valuable to threat actors.
To combat these threats, you must have policies, procedures, and technical safeguards in place to ensure the confidentiality, integrity, and availability of the EPHI under your control.
How Field Effect MDR helps secure private data
Field Effect’s Field Effect MDR is the ideal solution to rise to the challenge of thwarting hackers while maintaining HIPAA compliance. Here's how.
One section of the HIPAA legislation compels holders of EPHI to "protect against any reasonably anticipated threats or hazards to the security or integrity of protected electronic health information”. Most healthcare organizations don’t have the time or resources to monitor the rapidly evolving cyber threat landscape, which is why Field Effect MDR combines industry-standard indicators of compromise (IOCs) and our own threat intelligence to identify malicious systems, domains, botnets, ransomware, and other threats to our customers’ environments and patient data.
Another section states that EPHI holders must “identify and respond to suspected or known security incidents; mitigate, to the extent practicable, harmful effects of security incidents known to the covered entity or business associate”. Powered by sophisticated technology that monitors for cybersecurity threats on the endpoint, network, and cloud, Field Effect MDR reports on incidents that matter, without the deluge of threat alerts common to nearly all other cybersecurity products. In addition, Field Effect MDR can take action to lock cloud accounts and isolate systems to stop breaches before they impact EPHI.
Integrated ARO mappings
Field Effect MDR delivers reporting to our customers through our proprietary threat alerting system of Actions, Recommendations, and Observations. AROs provide high-confidence alerts combined with actionable insights that allow organizations to easily understand the response required.
Field Effect MDR users can enable their AROs to contain insights and mappings to the compliance frameworks they care most about. Reach out to our team to learn what mappings are available now.
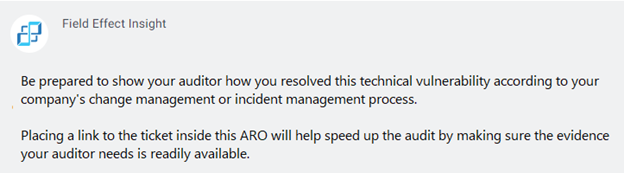
Here’s an example of a Field Effect Insight:
Learn more about Field Effect MDR & HIPAA compliance
We've created an easy-to-read mapping guide for HIPAA, which shows how Field Effect MDR can help our customers fulfill specific sections of the standard. This document is a great starting point to help you better understand the regulatory compliance landscape. But, because every organization is different, we still recommend consulting with a regulatory auditor for your specific requirements.
Reach out to our team for a copy of the HIPAA Compliance Mapping Guide.
