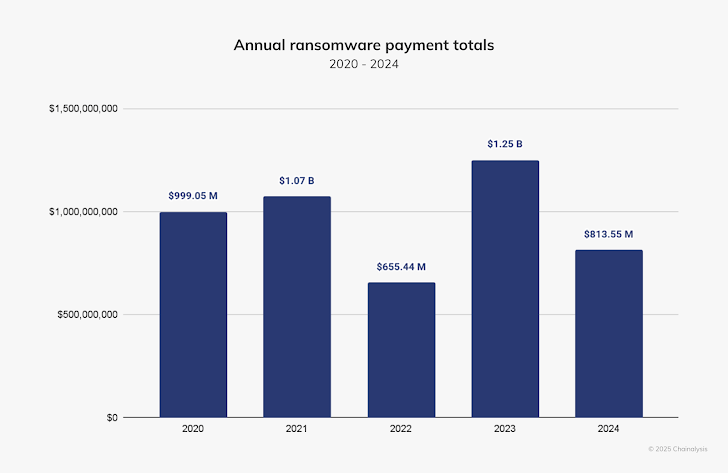
According to new research conducted by the blockchain analysis company Chainalysis, ransomware groups collected substantially less revenue from ransom payments in 2024. In total, ransomware victims paid a total of $813.5 million. This is down $436.5 million from 2023, making 2024 the first year since 2022 that ransomware revenues declined.
The researchers believe that for the most part, these revenues are down because victims have grown distrustful of ransomware actors actually decrypting data or deleting it from their possession and thus are less likely to pay ransom unless they have no other choice.
Chainalysis also credits law enforcement agencies for dismantling cybercriminal networks and crypto laundering services, which served to deny ransomware groups from accessing their infrastructure and funds.
While this downward trend in the total ransom payment amount seems optimistic, the company also noted that the frequency of attacks increased by 15% over 2023. In total, there were 5,263 successful ransomware attacks, over half of which compromised entities based in North America.
The most common ransomware variants observed during 2024 were:
- Akira (11%)
- Fog (11%)
- RansomHub (8%)
- Medusa (5%)
- BlackSuit (5%)
- BianLian (4%)
- Black Basta (4%)
Chainalysis believes this increase in overall ransomware attacks is due to the fall of two major ransomware groups, LockBit and BlackCat. Their collapse paved the way for the emergence of new ransomware actors that favor launching more attacks on smaller organizations, from which they tend to demand more modest ransom amounts, as opposed to fewer attacks on larger targets.
Source: The Hacker News
Analysis
While it’s positive that victims of ransomware attacks are paying less in ransom overall, it’s alarming to see a 15% increase in successful attacks over a year. These figures indicate that ransomware groups are still actively targeting organizations, just with less financial success.
This increase also doesn’t factor in all the unsuccessful attack attempts blocked by would-be victims who didn’t fall for the threat actor’s tricks and sophisticated cybersecurity solutions like Field Effect MDR. This underscores the ongoing need for robust cybersecurity practices and the importance of not becoming complacent despite the reduction in ransom payments.
Another trend not noted in this report is the increase of ransomware-as-a-service (RaaS) offerings that are now available to aspiring threat actors. RaaS offers several benefits—at least from a cybercriminal perspective—by lowering the barrier to entry for launching ransomware attacks which allows threat actors with limited technical expertise to rent or purchase pre-built ransomware kits from developers.
This model also helps evade the efforts of law enforcement since the core ransomware developers don’t usually execute attacks themselves; instead, they sell or lease their malware to affiliates who carry out intrusions. The arrest or disruption of an affiliate usually does not significantly impact the RaaS as a whole.
A great example is Black Basta, a RaaS operation that surfaced in early 2022. It quickly became a major player, suspected of having links to Conti, a now-defunct ransomware group. Black Basta targets large enterprises, encrypts systems rapidly, and leaks stolen data to pressure victims into paying. It has been linked to high-profile breaches across multiple sectors, making it a key example of how RaaS models enable rapid growth and sustained attacks.
Regardless of the statistics, ransomware remains one of, if not the biggest, cybersecurity threat facing organizations and will continue to be as long as threat actors can financially profit from it.
Mitigation
Field Effect’s Security Intelligence professionals constantly monitor the cyber threat landscape for ransomware-related threats. Field Effect MDR users are automatically notified if ransomware is detected in their environment and are encouraged to review these AROs as quickly as possible via the Field Effect Portal.
While defending against ransomware attacks may seem intimidating, even a few simple, easy-to-implement best practices can help prevent attacks. Field Effect recommends that organizations adopt the following best practices:
Backup your data
Regular backups of sensitive and important information can help ensure business continuity during a ransomware attack. These backups should be stored somewhere different than the operational network so that they will not be encrypted during an attack, and thus can be used to restore devices.
Update and patch software
Regular patching, updating, and maintenance help protect against or eliminate known cybersecurity vulnerabilities in IT systems and is one of the most important steps you can take to improve your security.
Protect systems connected to the internet
Using a DNS firewall limits access to known malicious websites, helping to defend against potential social engineering attacks while blocking malicious code and securing access to cloud apps and corporate websites. Leveraging a virtual private network (VPN) can also help, giving workers a secure means of accessing corporate data or otherwise connecting to networks from remote locations.
Develop a culture of cybersecurity
Organizations should train employees to watch for and understand the tricks attackers use, spot and avoid potential phishing links, and flag requests for personal information or credentials.
Strong password policies, password managers, and multifactor authentication (MFA) also make it more difficult for threat actors to guess, brute force, or use stolen credentials.
Use a cybersecurity solution
Staying ahead of ransomware demands a view into what’s happening across your IT environment. Cybersecurity solutions like Field Effect MDR that detect and respond to suspicious activity across networks, end-user devices, and cloud services can help identify and mitigate potential threats early.
Related Articles
