A ransomware threat actor known as the Reichsadler Cybercrime Group was recently observed attempting to compromise at least one unpatched WS_FTP server vulnerable to CVE-2023-4044. The threat actor deployed an open-source tool called GodPotato on the compromised server, using it to escalate privileges and ultimately deploy ransomware created with a leaked LockBit 3.0 builder. Fortunately, the attack was unsuccessful for reasons that were not shared.
Yet even though the target files weren’t encrypted, the threat actor still left a ransom note demanding a payment of $500 by October 15.
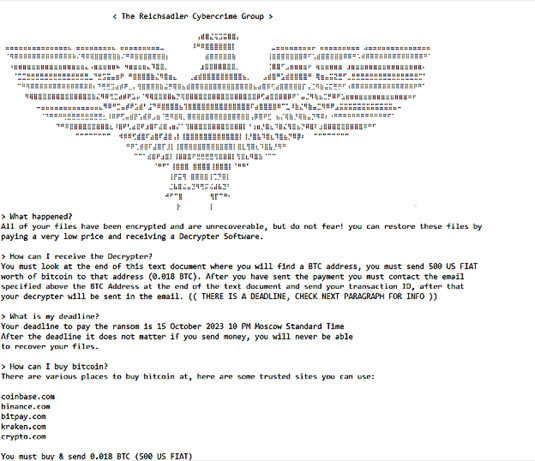
The attack comes less than two weeks after Progress Software, the maker of the MOVEit Transfer App, announced that it had discovered a critical vulnerability in its WS_FTP server software. The new maximum severity vulnerability, designated CVE-2023-4044, could enable a pre-authenticated threat actor to exploit a .Net deserialization vulnerability to execute remote commands. This flaw affects all WS_FTP versions prior to 8.7.4 and 8.8.2.
Source: Bleeping Computer
Analysis
Secure data transfer services, such as MOVEit and FTP servers, are popular targets for exploitation, given the nature of the data they secure and the list of organizations using them. Four of the 10 most popular secure file transfer services have been breached by threat actors. It appears WS_FTP can now also be added to that list.
It is noteworthy that the threat actor left a ransom note despite the unsuccessful attempt to encrypt the victim’s files. It’s possible that this attack was automated and errors in attack programming left the note.
Alternatively, this could suggest the attack was carried out by an inexperienced group. Regardless, attacks on unpatched WS_FTP servers are likely to accelerate as more threat actors develop their own exploits for CVE-2023-4044.
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities in software such as WS_FTP. This research contributes to the timely deployment of signatures into Covalence to detect and mitigate threat activity. Covalence users are automatically notified when vulnerable software, such as WS_FTP, is detected in their environment.
Field Effect recommends that organizations apply the appropriate mitigation measures and patch any affected versions of MOVEit Transfer and WS_FTP as soon as possible according to the instructions issued by Progress.
If your organization uses a secure data transfer service, ensure proper mitigations are in place to detect unauthorized access, misconfigurations, and data theft before a vulnerability is officially announced.
Related articles
