
Blog Post
May 16, 2025 | Cybersecurity education
By Field Effect
Research shows that a staggering 85% of organizations have experienced at least one social engineering attack. These attacks specifically target human vulnerabilities rather than purely technical weaknesses, meaning attackers attempt to exploit employees through manipulation and deception.
In this blog, we'll explore what social engineering attacks entail, the most common strategies hackers use, and actionable steps you can implement in response. Understanding these threats is the critical first step in building a robust "human firewall" and protecting sensitive data from exploitation.
Social engineering refers to attacks that manipulate individuals into voluntarily revealing sensitive information or unknowingly downloading malicious files. These threats leverage psychological manipulation—such as trust, urgency, fear, or curiosity—to deceive employees and gain unauthorized access.
For example, a hacker might send a convincing phishing email aimed at tricking an employee into sharing login credentials or opening an infected attachment. Once successful, cybercriminals can exploit this access to infiltrate your company’s internal networks, devices, or confidential databases.
Compared to highly technical exploits like zero-day vulnerabilities or denial-of-service (DoS) attacks, social engineering is relatively simple to execute. Essentially, anyone with malicious intent and persuasive communication skills can launch a social engineering attack.
Because these attacks rely heavily on human action—such as clicking links or downloading attachments—even a single employee's mistake can compromise a whole organization's security.
Cybercriminals use various tactics to infiltrate organizations through social engineering, but certain methods are more prevalent than others. Here are four of the most common types of social engineering attacks:
Phishing attacks try to lure an unsuspecting user into clicking a malicious link or file in an email. Hackers reach out to their victims from accounts that often appear trustworthy. They send messages that read like an official communication from a trusted person, company, or organization.
Phishing emails may look something like this:
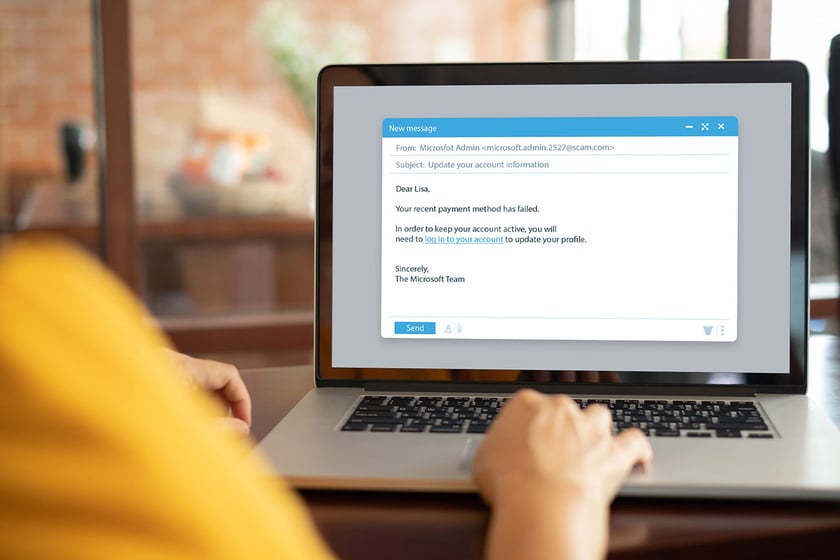
Once the victim clicks the link, they are directed to an illegitimate website or download malware that grants access to their device. The fake website prompts the user to input their username and password, and that info is sent directly to the hacker.
Basic phishing is largely a numbers game. Attackers often send the same generic email to hundreds or thousands of potential victims. They only need one recipient to click the link or input their credentials to be successful.
While phishing traditionally occurs via email, attackers now frequently use other channels, such as voice calls (vishing) and text messages (smishing), expanding their attack vectors.
Spear phishing is a more targeted and sophisticated version of phishing. Attackers research their intended victims extensively to create highly convincing emails.
For example, say a hacker wants to extract customer records from a company. They may start with LinkedIn to find an employee in the company’s customer success department. Then, the attacker could follow the person’s social trail to find a manager or colleague they probably receive emails from regularly.
At that point, the attacker sends an email to the victim that looks like it came from their manager or colleague. They often copy the person’s email address closely, hoping a busy employee accidentally overlooks the typos.
Here’s a simplified overview of how spear phishing attacks work:
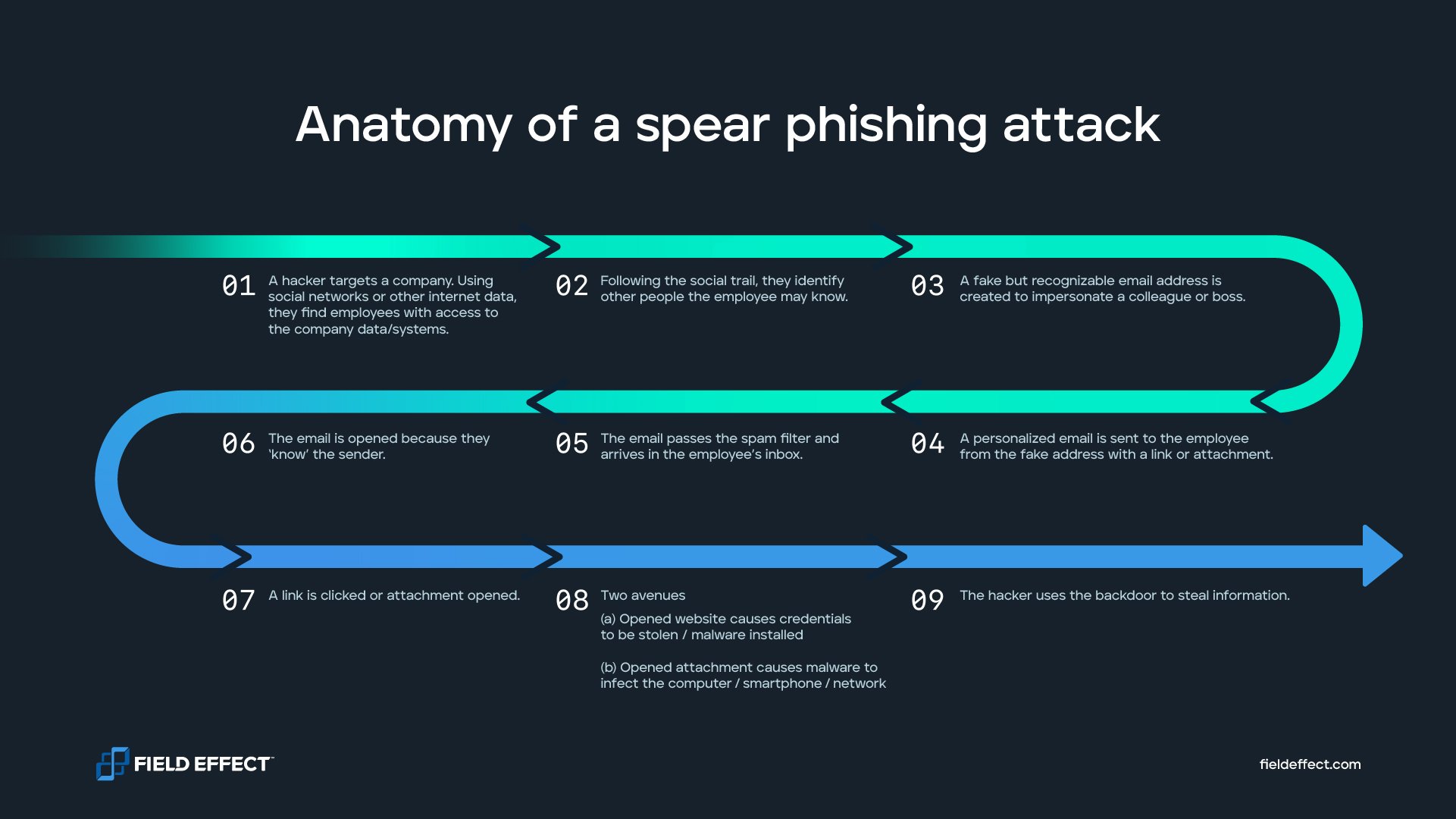
Due to how personalized and seemingly authentic messages like these are, victims are far likelier to click on them.
Business email compromise (BEC) is another scam that relies heavily on social engineering techniques. In a BEC attack, a scammer impersonates a trusted company executive or third-party vendor to initiate financial transfers to an account they own.
For example, they may pretend to be a security vendor updating payment instructions. The hacker would send a detailed email from an address that appears legitimate to the person within the organization who typically makes payments. But if this person follows the email’s instructions, the funds they send will go to the hacker.
BEC schemes can be incredibly damaging. According to the FBI’s latest Internet Crime Report, losses from BEC schemes exceeded $2.7 billion in 2022 alone.
Wild lions often wait by watering holes to catch unsuspecting prey. Hackers use a similar tactic to breach companies. With watering hole attacks, the cybercriminal picks an industry they want to target. Then, they find websites that people in that industry frequently use, such as message boards and forums.
These sites are “watering holes” that people within the industry keep coming back to for the resources they offer. The hacker will find and exploit vulnerabilities on these watering hole websites to inject malware. Just visiting the compromised website can infect users with malicious code.
Now that we've covered common types of social engineering attacks, let’s explore the tactics threat actors use to execute them. Understanding these methods can empower employees to better identify and defend against social engineering attempts.
Social engineering attackers frequently pretend to be authoritative figures known to the victim, such as a CEO, supervisor, or trusted colleague.
Using this false identity, attackers might request confidential information, sensitive company credentials, or even urgent financial transfers, exploiting trust and organizational hierarchies to achieve their goals.
Threat actors craft sophisticated messages designed to exploit a victim’s curiosity or professional interest.
For instance, hackers might promise fake sales leads, research findings, or other seemingly valuable information to entice employees. Attackers count on victims prioritizing their desire for information over security caution.
Creating a sense of urgency is a hallmark of many social engineering attacks. Hackers commonly send messages highlighting time-sensitive opportunities or urgent tasks that require immediate attention.
This pressure can lead employees to make impulsive decisions, like clicking links or downloading files, without critical consideration.
Attackers frequently exploit legitimate communications tied to current events or organizational announcements. Because such communications often follow predictable formats with consistent branding, they become easy templates for attackers to mimic convincingly.
Employees, expecting routine updates, might unwittingly interact with malicious content hidden within these familiar messages.
Social engineering attacks exploit basic aspects of human psychology, turning our natural instincts into vulnerabilities. Most people inherently trust their coworkers, supervisors, and reputable organizations. Additionally, many employees assume that malicious emails are automatically filtered out, believing any email reaching their inbox must be legitimate.
These attacks can be particularly challenging to detect and prevent because they don't rely on purely technical vulnerabilities. Instead, social engineering bypasses technological defenses by persuading trusted employees to willingly share sensitive information.
To reduce this risk, Field Effect recommends following the principle of least privilege—granting employees access only to the systems and tools essential for their daily responsibilities, rather than full access to all company technology.
Implementing this principle helps limit potential damage. If an employee inadvertently falls victim to a social engineering attack, the attacker gains access only to a restricted portion of sensitive data, protecting your organization from widespread compromise.
Some people think they’d never fall for a social engineering attack. But attackers can be very sophisticated. To illustrate just how powerful these attacks can be, consider the following examples.
A Lithuanian national recently used a social engineering attack to steal approximately $100 million from Google and Facebook. He created a fake company that looked like a real computer manufacturer Google and Facebook did business with.
The two companies received the services they requested from the actual computer manufacturer but paid their invoices to a fake account controlled by the scammers. The man successfully phished employees, from both companies, who were expecting invoices from the real vendor.
Robinhood was also the target of a recent social engineering attack. The threat actor managed to gain confidential credentials from a customer service representative by phone. This gave them access to the company’s customer databases, where they stole sensitive information on about 7 million Robinhood users.
Years ago, hackers targeted Twitter employees in a sophisticated spear phishing campaign. The scam worked, and hackers accessed the social media accounts of high-profile figures and corporations, including Barack Obama, Elon Musk, and Apple.
The hacker used this access to post Bitcoin scam links from trusted accounts. They’re said to have stolen over $100,000 in the attack.
An update from Twitter said that the hackers social-engineered a small number of Twitter employees over the phone. The company notes that the attack exploited human vulnerabilities to access Twitter’s internal systems.
Social engineering poses a significant threat to businesses of all sizes. However, with proper education, proactive measures, and strategic investments, it's easy to strengthen an organization’s cybersecurity posture and protect sensitive information.
Here are several effective strategies to get us started:
Social engineering attacks are carefully designed to exploit human psychology and naiveté. Make the attacker's life a little harder by teaching employees about the common characteristics these attacks share.
Technical indicators of a malicious email may include:
Behavioral indicators include:
Staying informed about the latest social engineering tactics through news and industry updates will further strengthen preparedness.
Encourage employees to verify information independently if they encounter suspicious or unusual requests.
For example, if a vendor suddenly emails to ask an employee to pay an invoice to a new account, the employee should confirm it’s real before paying. That could mean contacting the person making the request by phone or verifying the invoice's validity by email with another trusted member of the organization.
In fact, it may be helpful to set up a mandatory verification process for events like this. Anytime suppliers, vendors, or providers ask for changes or payment, you could ask employees to always verify the request through another medium before proceeding—even if they feel confident in the request’s legitimacy.
Do new employees automatically have broad access to the company's resources? Limiting employee access to only essential systems and databases—the principle of least privilege—can minimize potential damage in case of a breach.
By restricting access, you ensure that a successful social engineering attack affects only a limited portion of data, making containment and recovery more manageable.
Hands-on training through phishing simulations is an effective method to prepare your employees against social engineering threats. Providers like Field Effect offer tailored phishing simulation services using realistic scenarios and advanced social engineering techniques.
Post-simulation reports provide valuable insights into your organization's vulnerabilities, enabling targeted improvements and heightened readiness against real-world threats.
Finally, consider setting up more sophisticated technical protections if you’re worried about social engineering attacks impacting your organization. Many companies offer 24/7 threat monitoring services that identify and address anomalies in behavior before attackers can cause serious damage or disruption.
Without any technical protection, a hacker who launches a successful social engineering attack could access your network for a long time without your knowledge. But with the right monitoring tools, you could identify the hacked account almost immediately and take action to quarantine it before the threat actor has the chance to wreak havoc.
Social engineering attacks can seem difficult to identify and prevent because of the human factor. But you can manage this risk just like you manage other security concerns.
That process starts by training your employees. Our 2025 Employee Cybersecurity Handbook is perfect for this. It features everything your team needs to know about cybersecurity and social engineering.
You can share the report with your employees or get in touch with us to learn more about Field Effect MDR, our holistic cybersecurity solution that helps companies of all sizes deal with the widest range of cyber threats, including social engineering attacks.


