Cybersecurity researchers have discovered a new campaign targeting 70 organizations in the insurance, aerospace, transportation, and education sectors with a backdoor dubbed ‘Voldemort’.
The backdoor is being delivered via clever phishing emails that impersonate the target country’s tax agency and claim to have updated tax information needing the target’s review.
When the target clicks the link, they are redirected to a Windows Search Protocol Uniform Resource Identifier (URI) that triggers Windows Explorer to display an LNK or ZIP file disguised as a PDF. By using the Windows Search Protocol URI, the threat actor can make the destination file appear as if it resides locally in the target’s Downloads folder, making it more likely the target will click it.
Once the file is clicked, a Python script performs system profile collection, a decoy PDF is displayed to the victim, and a legitimate copy of Cisco WebEx and a malicious DLL are downloaded to enable the Voldemort backdoor via DLL-sideloading.
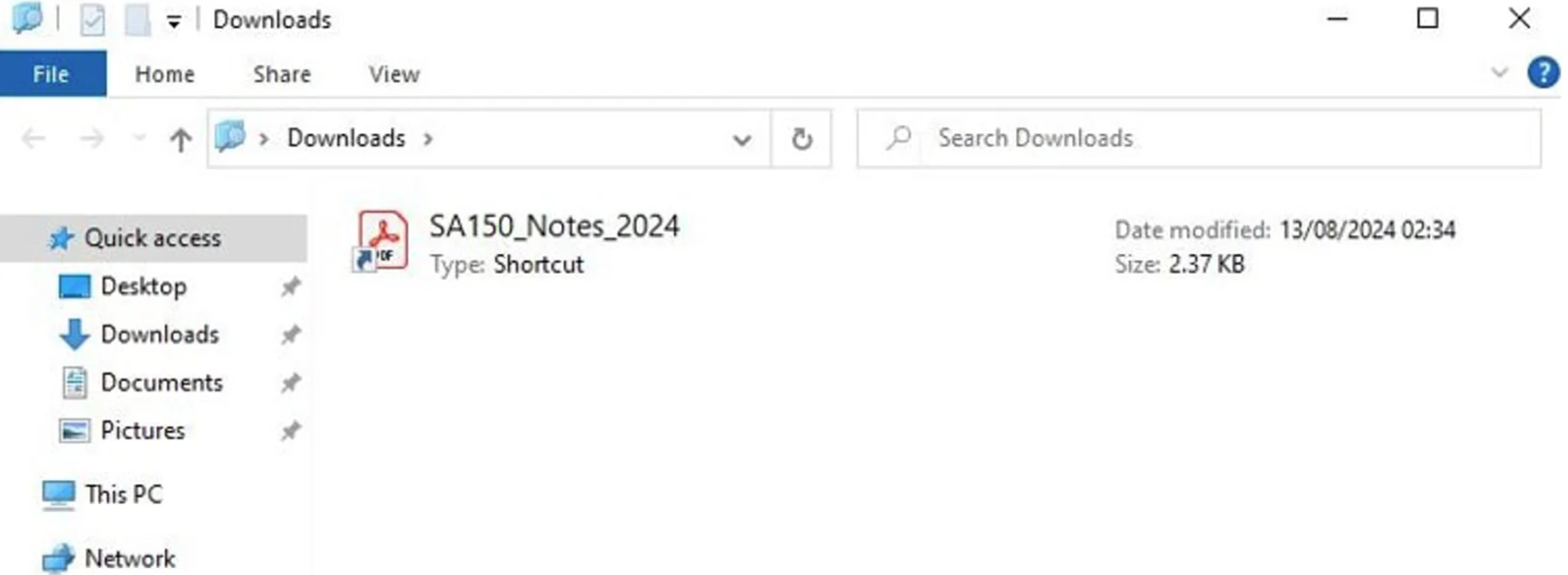
Image 1: Windows Search Protocol URI making the file appear as if it resides locally.
The backdoor is capable of a wide range of functions including exfiltrating and modifying files and downloading new payloads. Interestingly, Voldemort relies on Google Sheets as its command and control (C2) infrastructure by using Google’s API with the embedded client ID, secret, and refresh token stored in the backdoor’s encrypted configuration. This technique offers reliable and highly available C2 infrastructure with whom communication is unlikely to be flagged by security tools.
The threat actor behind the campaign is currently unknown, but researchers believe its objective is likely to conduct cyber espionage.
Source: Bleeping Computer
Analysis
The impersonation of governmental agencies, such as tax departments, is an effective way to create urgency, an element required for a successful social engineering attack.
In the campaign above, the victim would be highly motivated to view the supposed documents since they could have an impact on the company’s bottom line or indicate that the company has violated tax requirements.
The threat actor was also patient enough to craft the phishing emails to impersonate the tax agency of the country the target was in, and written in the relevant language, to add further legitimacy to the emails.
The abuse of Google Sheets as the backdoor’s C2 infrastructure not only allows Voldemort’s traffic to blend in, but makes it particularly difficult for organizations that use Google Sheets as their IT administrators won’t easily be able to block malicious traffic even if it is detected.
Given that the campaign began in early August and no victims have yet had their data extorted or ransomed, the researcher’s assessment of the threat actors being espionage-motivated is likely correct.
Mitigation
Field Effect’s Security Intelligence team constantly monitors the cyber threat landscape for emerging threats like the Voldemort backdoor. This research contributes to the timely deployment of signatures into Field Effect MDR to detect and mitigate the risk these threats pose.
Field Effect MDR users are automatically notified when various types of malicious activities are detected in their environment and are encouraged to review these AROs as quickly as possible via the Field Effect Portal.
Field Effect recommends that users scrutinize all unsolicited messages from untrusted sources via email, text, or social media, especially when those messages contain a link or attachment. Field Effect MDR users are encouraged to submit suspicious emails to our Suspicious Email Analysis Service (SEAS) to ensure they are benign before interacting with them.
Related Articles
