Unknown threat actors have recently been observed targeting organizations in the Middle East with malware disguised as Palo Alto Networks’ GlobalProtect virtual private network (VPN) tool.
Researchers suspect that attacks begin with a phishing email enticing the recipient to download and install what claims to be a GlobalProtect agent setup file. However, in addition to installing the actual agent, the setup file also installs a backdoor.
Once installed, the backdoor immediately establishes communication with threat actor-controlled infrastructure to send updates on its process. It also drops two other files, RTime.conf and ApProcessID.conf, that are responsible for sending information related to the compromised system, such as its IP address, operating system version, etc. Once instructed by its controllers, the backdoor can execute PowerShell, exfiltrate data, and download further payloads.
To help obscure the traffic it generates, the backdoor communicates with unique, newly registered URLs containing the string 'sharjahconnect', which resembles a legitimate VPN portal for a UAE-based company, allowing it to blend in with expected regional network traffic.
Source: The Hacker News
Analysis
While researchers suspect that phishing is likely the primary attack vector, it’s also possible that the threat actors are using malicious search engine optimization (SEO) techniques or sponsored ads to deploy the backdoor.
For example, a quick Google search for ‘Palo Alto GlobalProtect tool download’ lists multiple non-legitimate websites claiming to offer this tool for download. Any of these sites could potentially serve malicious downloads to unsuspecting users.
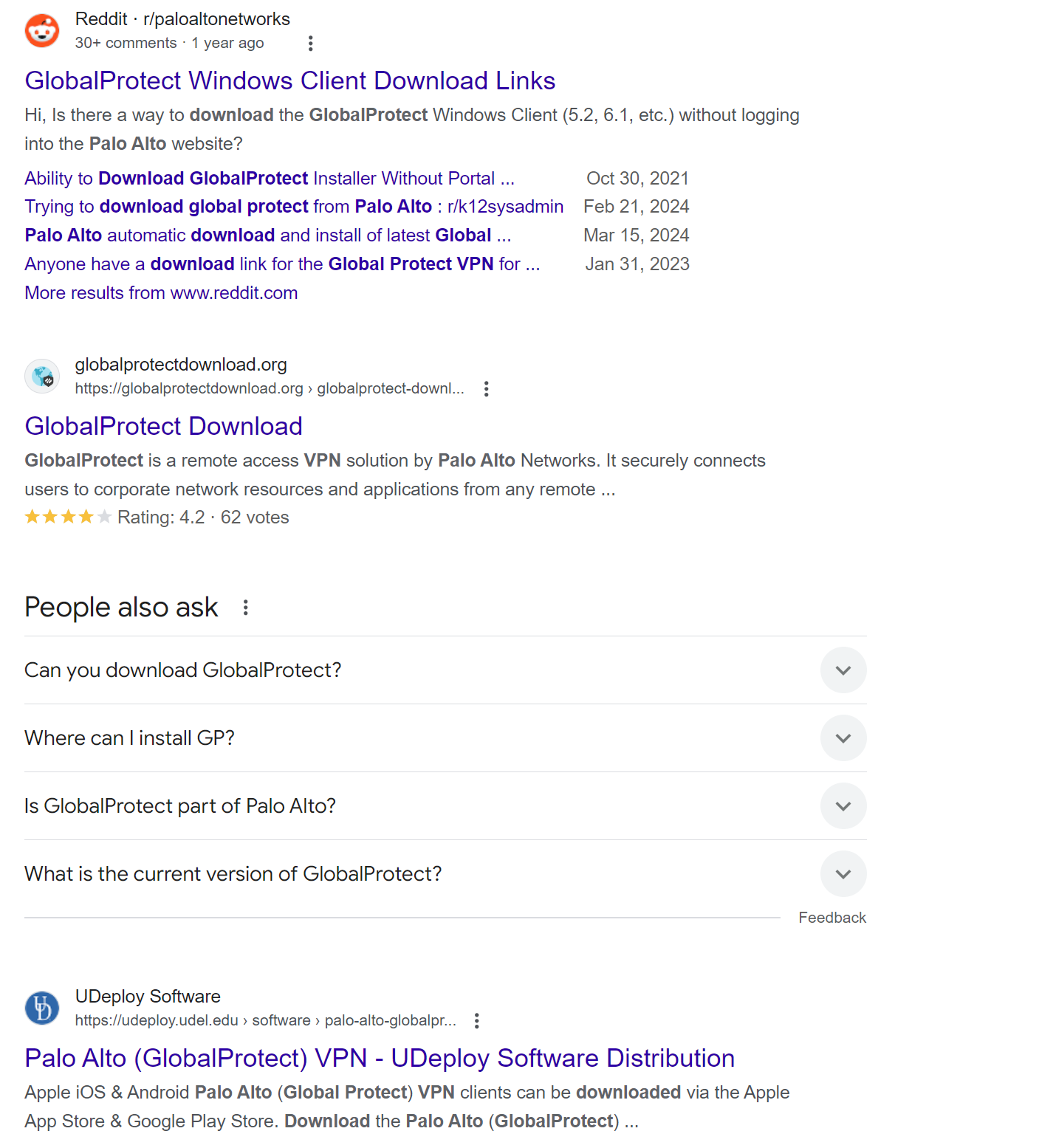
Image 1: Search results for GlobalProtect VPN tool (Source: Google)
Field Effect discovered a similar campaign in 2023 in which trojanized ads for a Webex download file were responsible for the installation of IcedID malware.
Regardless of the initial attack vector, it’s likely that the threat actor had identified that the primary targets of its campaign were users of, or are interested in, GlobalProtect VPN, and thus chose this software to disguise.
Mitigation
Field Effect’s Security Intelligence team constantly monitors the cyber threat landscape for emerging tactics, techniques, and procedures used by threat actors. This research contributes to the timely deployment of signatures into Field Effect MDR to detect and mitigate the risk these state-sponsored cyber actors pose.
Field Effect MDR users are automatically notified when various types of malicious activities are detected in their environment and are encouraged to review these AROs as quickly as possible via the Field Effect Portal.
Field Effect recommends that users remain aware of threat actors’ ability to masquerade legitimate software and scrutinize the source of software they intend to download and install. Check for things like spelling mistakes, poor grammar, typo-squatted domains, and inconsistent branding and stick to software from trusted sources, such as the vendor’s own website or their company’s software portal.
Related Articles
