Palo Alto is currently investigating a ‘potential’ remote code execution (RCE) vulnerability in the PAN-OS management interface used by the company’s firewalls. The company advised that, so far, its investigation into the claimed vulnerability hasn’t revealed any signs of active exploitation.
Nonetheless, it recommends that impacted users ensure the PAN-OS management interface is configured correctly. Palo Alto also advised affected customers to restrict Internet access to and only allow connections from trusted internal IP addresses.
The news of this potential RCE bug comes just a week after the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned that a critical missing authentication vulnerability in Palo Alto Networks Expedition, designated CVE-2024-5910, was being exploited by threat actors to reset application admin credentials on Internet-exposed Expedition servers.
CISA has added CVE-2024-5910 to its Known Exploited Vulnerabilities Catalog and issued an order for federal agencies to secure their systems by November 28.
Source: Bleeping Computer
Analysis
In the absence of a formal CVE designation, the potential flaw is being referred to as ‘PAN-SA-2024-0015’, the ID associated with the alert Palo Alto issued regarding it. Field Effect is unable to determine the exact origin of the claimed vulnerability.
However, given that Palo Alto firewalls serve as the first line of defense for many organizations, a potential RCE vulnerability could pose a significant cybersecurity risk. Exploitation of an RCE bug could allow threat actors to modify firewall rules, enabling unrestricted access to the target’s network.
According to the Shadowserver Foundation, there are nearly 11,000 instances of PAN-OS management interfaces exposed to the internet and could be vulnerable to PAN-SA-2024-0015.
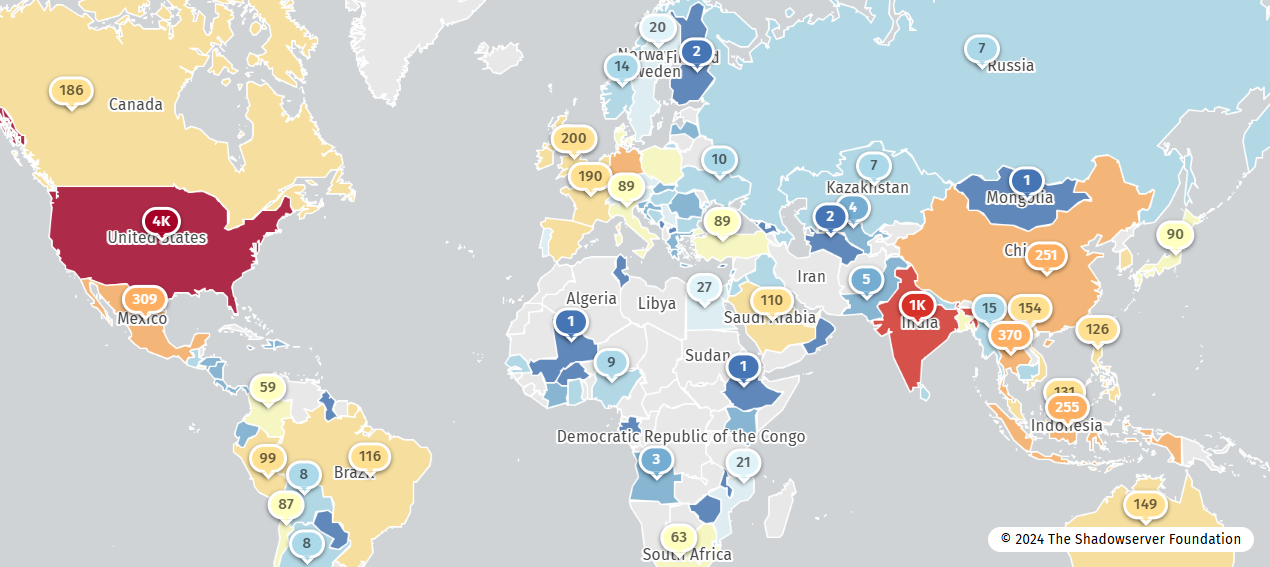
Hopefully, Palo Alto concludes its investigation quickly and, if a vulnerability is found, patches it before threat actors have a chance to exploit it.
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities discovered in software, appliances, and operating systems. This research contributes to the timely deployment of signatures into Field Effect MDR to detect and mitigate the exploitation of these vulnerabilities.
Field Effect MDR users are automatically notified when vulnerable software is detected in their environment and are encouraged to review these AROs as quickly as possible via the Field Effect MDR portal.
Field Effect strongly encourages users of potentially vulnerable Palo Alto firewalls to ensure the management interface is configured properly by following the guidance in Palo Alto’s advisory.
Related Articles
