The same security researchers who responsibly disclosed a vulnerability in CrushFTP have now publicly released proof-of-concept exploit code, putting pressure on nearly 10,000 users to update their software quickly.
Making matters worse, the researchers believe that threat actors have been able to develop their own code by reverse engineering the patch provided by the vendor, and may even be capable of exploiting patched instances.
The vulnerability, designated CVE-2023-43177, was originally discovered in August 2023 and then patched in CrushFTP 10.5.2 which was released 24 hours later. The vulnerability resides in CrushFTP’s enterprise suite and allows threat actors to access files on the server, execute code, and obtain plain-text passwords without authentication.
Source: Bleeping Computer
Analysis
Field Effect was not able to confirm the referenced 10,000 public-facing CrushFTP deployments. Instead, our research indicates there are just over 3,000, with the majority located in the US. This number doesn’t include deployments behind firewalls inaccessible to our scanner.
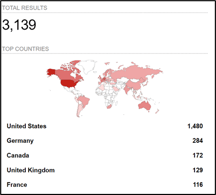
Image 1. Scan results for CrushFTP deployments. (Source: Shodan.io)
The exploitation of vulnerabilities in secure file transfer and storage applications has been extremely common in 2023. This is likely due to the nature of the data they secure and the long list of organizations using them. For example, in May 2023, a critical zero-day vulnerability allowed unauthenticated threat actors to gain unauthorized remote access to thousands of MOVEit Transfer databases belonging to prominent governments such as Canada and the US, and organizations such as Shell and British Airlines.
In addition to exfiltrating sensitive information, threat actors including Cl0p deployed ransomware on compromised MOVEit services, causing victims additional headaches.
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities discovered in software such as CrushFTP. This research contributes to the timely deployment of signatures into Covalence to automatically notify users when vulnerable software is detected in their environment. Additionally, Covalence will automatically notify users when unauthorized data theft/loss is detected. Users are encouraged to review these AROs as quickly as possible.
Field Effect strongly encourages users of CrushFTP to update to the latest version as soon as possible.
If your organization uses a secure data transfer/storage service, ensure proper mitigations are in place to detect unauthorized access, misconfigurations, and data theft before a vulnerability is officially announced.
Related articles
