SonicWall has released a patch to address a critical vulnerability recently discovered in several firewall devices that run SonicOS.
The flaw, designated CVE-2024-40766, is described as an improper access control vulnerability that could potentially allow threat actors to access resources without authorization and/or cause the affected device to crash. SonicWall hasn’t indicated whether it was aware that the vulnerability was being actively exploited.
SonicWall is advising impacted users to install the relevant updates as soon as possible. Users who can’t apply updates immediately are encouraged to restrict management access of the device to local, trusted sources.
Source: Bleeping Computer
Analysis
Since CVE-2024-40766 was announced on August 23, Field Effect has observed increased targeting of SonicWall firewalls. However, further analysis is required to determine if threat actors specifically targeted CVE-2024-40766 in these incidents or other, older, unpatched vulnerabilities. It’s possible that the news of CVE-2024-40766 drew the attention of threat actors toward exposed SonicWall devices in general.
SonicWall firewalls are very popular among critical infrastructure industries and corporate environments and are thus frequently targeted by threat actors looking to obtain initial access into networks of interest. According to the Shadow Server Foundation, approximately 400,000 SonicWall deployments are deployed worldwide, representing a significant potential attack surface for threat actors with SonicWall exploits.
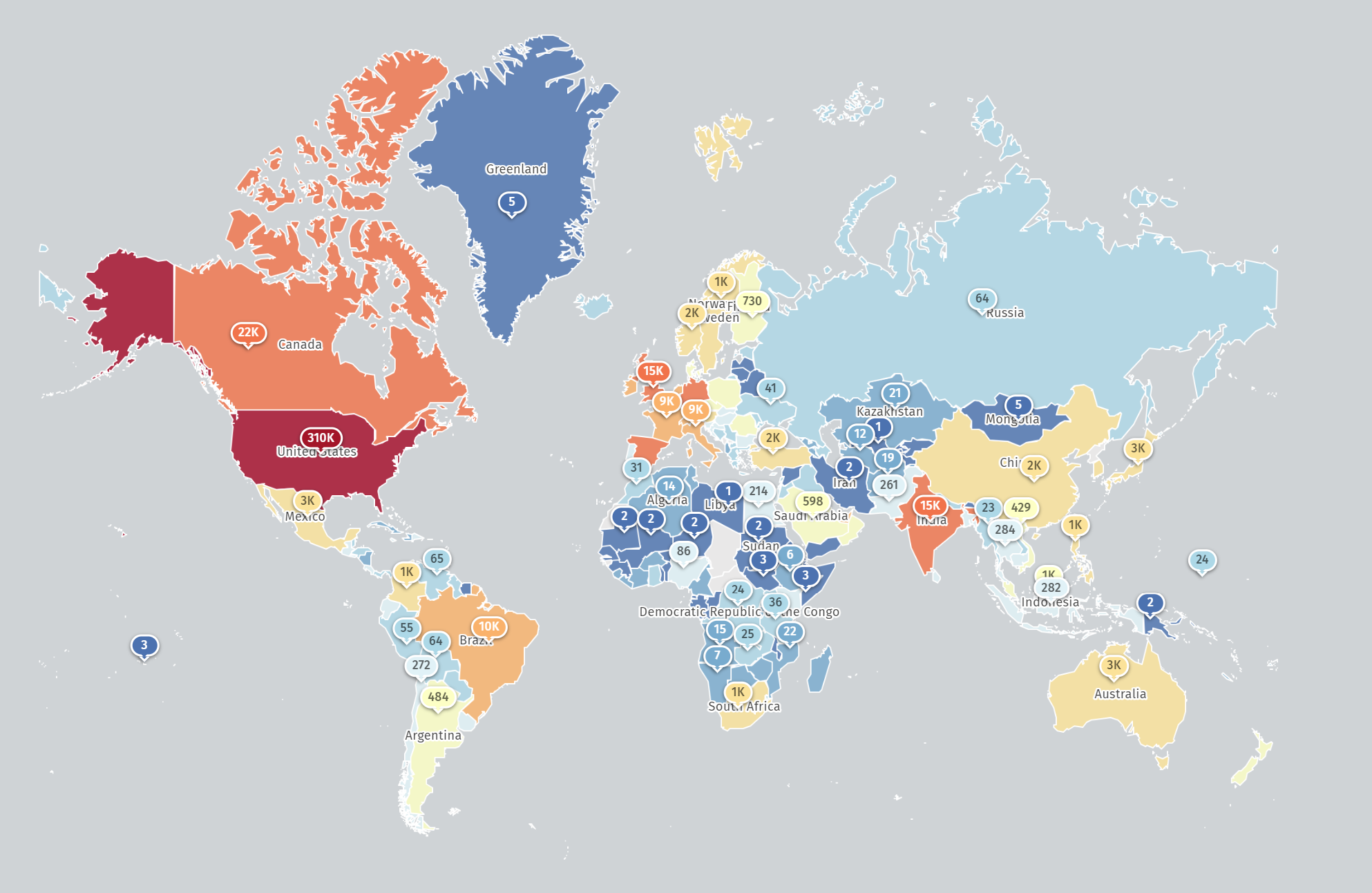
SonicWall firewall deployments (Source: Shadow Server Foundation)
Mitigation
Field Effect’s Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities discovered in firewalls like SonicWall. Field Effect MDR users are automatically notified if vulnerable software is detected in their environment and are encouraged to review these AROs as quickly as possible via the Field Effect Portal.
Field Effect strongly recommends users of the affected SonicWall firewall versions update to the latest version as soon as possible, in accordance with the advisory.
Related Articles
