Security researchers have observed unnamed threat actors exploiting a critical vulnerability in the widely adopted self-hosted file-sharing platform, ownCloud. The bug, designated CVE-2023-49103, exposes admin passwords, credentials, and license keys which can leveraged by threat actors to exfiltrate data from the ownCloud server.
On November 21, ownCloud released three security bulletins containing mitigation instructions for CVE-2023-49103 and two other less severe vulnerabilities. However, just four days later, mass exploitation of CVE-2023-49103 was observed by multiple security researchers.
Researchers estimate at least 11,000 vulnerable instances of ownCloud are deployed worldwide, with the majority in the US, Germany, and Russia.
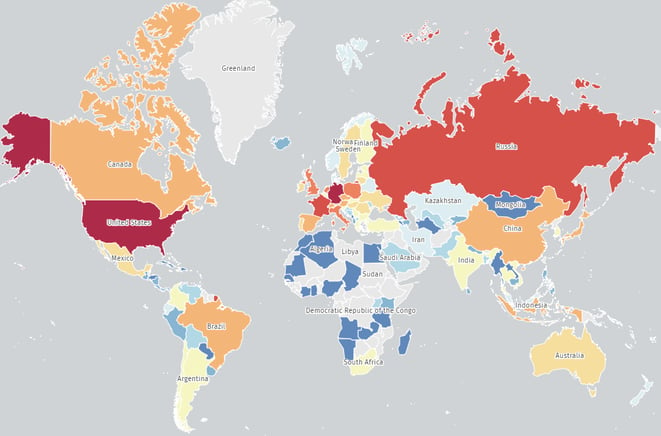
Image 1: Heatmap of vulnerable ownCloud deployments
ownCloud is urging administrators to make immediate mitigative efforts to reduce the risk associated with CVE-2023-49103. Rather than simply patching, ownCloud recommends that admins delete the owncloud/apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php file, disable the phpinfo function in Docker containers, and rotate admin passwords, mail server and database credentials, and Object-Store/S3 access keys.
Source: Bleeping Computer
Analysis
It would appear that ownCloud can now be added to the long list of secure file storage and transfer applications that have been exploited in 2023. These applications remain popular with threat actors due to the nature of the data they secure/transfer and the variety of organizations using them.
For example, in May 2023, a critical zero-day vulnerability allowed unauthenticated threat actors to gain unauthorized remote access to thousands of MOVEit Transfer databases belonging to prominent governments such as Canada and the US and organizations like Shell and British Airlines.
In addition to exfiltrating sensitive information, some threat actors like Cl0p took the opportunity to deploy ransomware on compromised MOVEit services, causing victims additional headaches.
Mitigation
Field Effect’s elite team of Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities discovered in software such as ownCloud. This research contributes to the timely deployment of signatures into Covalence to detect and mitigate the exploitation of these vulnerabilities. Covalence users are automatically notified when vulnerable software is detected in their environment and are encouraged to review these AROs as quickly as possible.
Field Effect strongly encourages users of ownCloud to implement the mitigation recommendations as soon as possible.
If your organization uses a secure data transfer/storage service, ensure proper mitigations are in place to detect unauthorized access, misconfigurations, and data theft before a vulnerability is officially announced.
Related articles
