Palo Alto Networks (PAN) has released patches to address multiple vulnerabilities recently discovered in its Expedition tool which is used to facilitate the migration of users from other firewall vendors to its own. While the flaws vary in severity, each could potentially allow threat actors to access sensitive information such as credentials and session IDs.
The most severe of the five vulnerabilities, designated CVE-2025-0103, is a SQL injection vulnerability that could allow threat actors to read Expedition database contents and create and delete arbitrary files on the Expedition system. The files could potentially include information such as usernames, cleartext passwords, device configurations, and device API keys for firewalls running PAN-OS software.
The other vulnerabilities include a cross-site scripting flaw, arbitrary file deletion, wildcard expansion, and command injection.
The discovery of these five vulnerabilities comes as the Expedition tool reached end-of-life status on December 31, 2024. Fortunately, PAN has already addressed the flaws in the latest version of Expedition’s firmware which was released before the tool reached end-of-life status. Users who have not updated are encouraged to do so and to ensure all access to Expedition is restricted to only authorized users, hosts, and networks, or disabled if it's not in use.
Source: The Hacker News
Analysis
The compromise of migration software, such as PAN’s Expedition tool, could result in the disclosure of credentials and other data that threat actors can use to facilitate future attacks on other infrastructure to which the credentials grant access. Thus, it’s crucial for organizations to apply security patches and updates promptly to these tools, follow best practices for their secure configuration and monitor for any signs of exploitation to mitigate potential risks.
This isn’t the first time vulnerabilities have been discovered in PAN’s Expedition tool. In November 2024, the Cybersecurity and Infrastructure Security Agency (CISA) warned of active exploitation of critical vulnerabilities in Expedition, including CVE-2024-9463 and CVE-2024-9465, that allowed threat actors to execute arbitrary commands and gain unauthorized access to sensitive data.
Fortunately, it appears that only a few instances of Expedition—11, according to Shadow Server—remain exposed to the open internet, limiting the attack surface available to threat actors. However, this small number of potentially vulnerable Expedition services will likely be targeted for exploitation very soon, if they haven’t already.
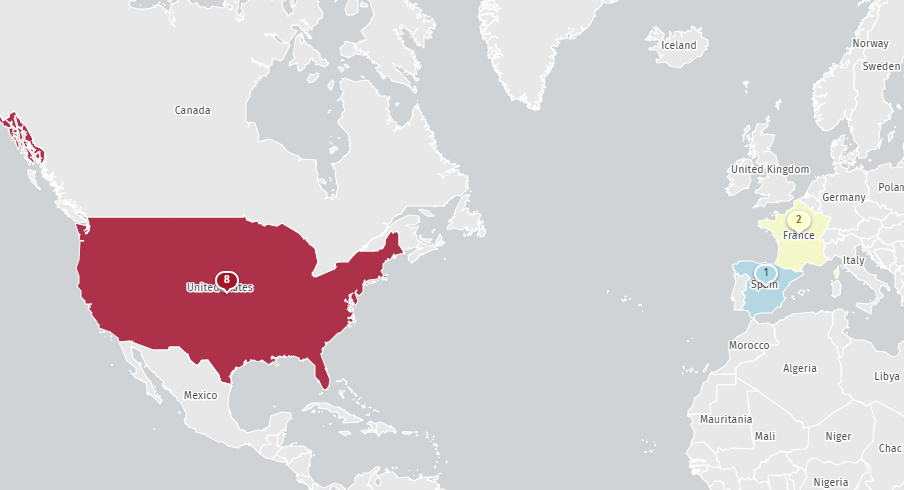
Internet exposed instances of PAN Expedition (Source: Shadow Server)
Mitigation
Field Effect’s Security Intelligence professionals constantly monitor the cyber threat landscape for vulnerabilities discovered in software like Expedition. Field Effect MDR users are automatically notified if vulnerable software is detected in their environment and are encouraged to review these AROs as quickly as possible via the Field Effect Portal.
Field Effect strongly recommends users of the PAN Expedition to update to the latest version as soon as possible, in accordance with the advisory.
Related Articles
